Capturing SQL Traffic from SSH Tunnel Sessions Over Standard Ports
The following section describes how to enable SQL Traffic to be recorded to a session’s Session Event report when the tunnel is using standard ports (for example, port 3306 for MySQL or port 1433 for MS SQL).
It is assumed that an SSH Tunnel session is already configured properly in Privileged Access Management.
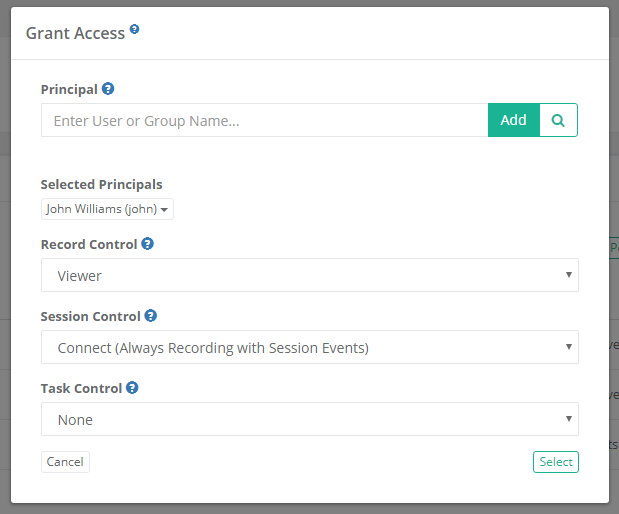
- Navigate to the record that is being used to create your SSH Tunnel session and open its Permissions (Manage > Permissions).
- Assign one of the with Session Events permissions levels to your user or group. If this record inherits its permissions from a parent, then modify the parent object’s permissions as needed.
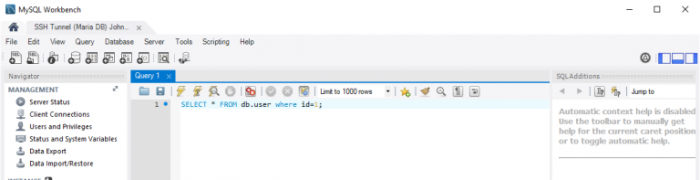
- Open an Privileged Access Management SSH Tunnel session using this record with this assigned user and perform some SQL commands to test the event capture.
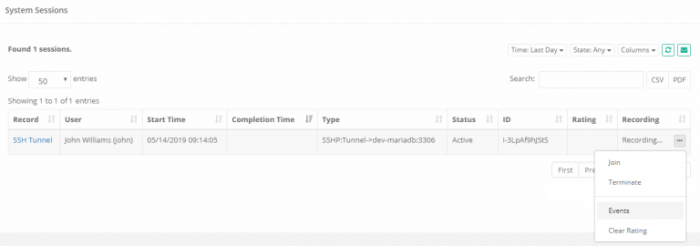
- While the session is still active (or you may complete the session), navigate to this record’s Session report and choose Recording > Events to open the Session Events report.
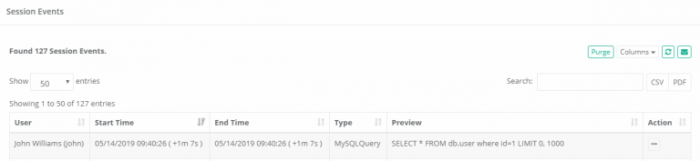
- Observe that your executed SQL statements were captured to the Session Event log.
Capturing SQL Traffic from SSH Tunnel Sessions Over Non-Standard Ports