Active Directory Integration
To integrate your Active Directory with PAM, you may configure your settings during or after installation.
PAM does not have any limitation on the version or functional level of Active Directory. It is recommended to use a version that uses TLS 1.2.
If you are looking to integrate with additional AD or LDAP domains, please review our Multi-domain Configuration article.
If you are looking to integrate with NetIQ eDirectory, please review our NetIQ eDirectory Integration article.
We recommend using an Active Directory account whose password does not change. If the password of this account does change, PAM’s integration with your Active Directory will no longer work resulting in AD users being unable to login to PAM. If your AD integration account password does change, then you can follow the procedure outlined in the section To configure or update an Active Directory binding After Installation on this page to update PAM with your new password.
Active Directory binding During Installation
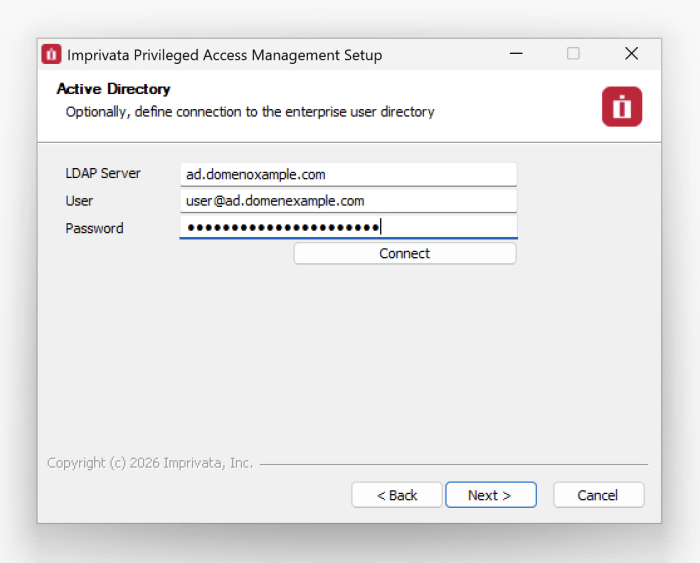
To configure an Active Directory binding During Installation:
- When the installation wizard reaches the section named Active Directory enter the following values:
LDAP Server: Enter the host name or IP address of your Active Directory Domain Controller.
User: Enter the user name of the account that can connect to this server.
Password: Enter the password of this user.
-
Click the Connect button to test your connection.
-
If the test connection was successful, click the Next button to continue. If the test connection failed, check your values and try again.
Active Directory binding After Installation
To configure or update an Active Directory binding After Installation:
(June 4, 2018) – If you have updated to PAM version 2.3.201806032154 or later, you can now configure Active Directory integration by simply navigating to Administration > Settings > AD within the PAM interface.
-
Login to the server where PAM is deployed as an Administrator.
-
Open a command line and navigate to the folder where PAM is installed ($PAM_HOME) and issue the following command:
- for Windows, substitute your ldap.server, ldap.user and ldap.password values and issue:
-
for Unix or Linux, substitute your ldap.server, ldap.user and ldap.password values and issue:
Copybin/PamDirectory.sh ADConnect web ldap.server ldap.user ldap.password If the command returns an OK response, then restart the PamManagement (Windows) or pammanager (Linux) service on this computer:
- for Windows:
for Unix or Linux:
If the command returns a Fail response, then double check your user and password values. For the {ldap.user} value, be sure to use the user@domain format.
Active Directory integration is now complete. Objects and permissions may now be shared with AD Users and Groups in PAM.
bin\PamDirectory.cmd ADConnect web ldap.server ldap.user ldap.password
Please note if your password contains any of the following characters & \ < > ^ | then they must be properly escaped when executing the command by placing a ^ before each like this for ampersand ^&. Alternatively, you can issue the command using a dash – rather than the password in which case you will be prompted to enter the password during execution and in this approach, those special characters do not have to be escaped.
net stop PamManagement
net start PamManagementservice pammanager restartTo support self-password reset in PAM for your AD users, you must configure your AD integration using LDAPS and the defined LDAP binding account must be able to reset the password of other users in this Active Directory