Generate Temporary AWS API Keys
Generate Temporary AWS API Keys for Privileged Users, Applications, Command Line and Automation.
PAM can generate AWS STS Temporary AWS API access keys (Access Key Id and Secret Key pair) for a specified duration based on the provided superuser access keys, those of which are stored safely in the PAM Identity Vault.
The option enables Just in Time access for users, applications, command line utilities and automation software to communicate with Amazon Web Services with least possible standing privileges.
Generate an AWS API Key Pair for Temporary Access
- First, we must enable the functionality, so login to PAM with a System Administrator account. A System Administrator account is only needed to enable the Record Type, not to manage or generate keys once it is configured.
- Navigate to Administration > Record Types and locate the record type AWS STS Temporary Access. Click it Edit button, uncheck the Hidden option and click Save. This will unhide and make available to users’ this record type. After this step, you will no longer need to use System Administrator access.
- Navigate to All Records and into a container where you want to generate these temporary access keys. In this container, click the New Record option and select this type AWS STS Temporary Access from the dropdown menu.
- Create the record as needed.
Name: Enter a recognizable name.
Description: Optionally, enter a description.
Access Key ID: Enter your superuser’s AWS Access Key ID.
Secret Key: Enter your superuser’s AWS Secret Key.
Duration: Optionally, define a length of time (in seconds) for which this key will be valid. The value must be between 900 and 129600 seconds.
-
Click Save and Return to create your record.
After the record is created, you can use the record’s Execute > AWS STS Temporary Ticket Generator option to generate your on-demand temporary key pair.
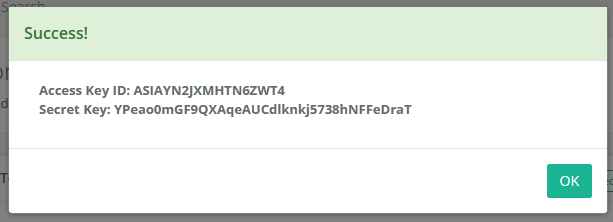
When a temporary key pair is generated, a new event will be created in the Audit Log:
- Time: <when the key was generated>
- User: <who generated the key>
- IP: <the user’s IP address at the time the key was generated>
- Category: Data
- Level: INFO
- Event: AWS STS Temporary
- Message: AWS STS Temporary Key Generated.
- Region: <region>, duration: <duration>
Additional Configuration Options
PAM System Administrator may include extended options when enabling this record type through the use of additional fields.
The following fields, when added to this AWS STS Temporary Access record type, extends the functionality of this feature.
Role ARN field can be added to the record type to enable Assume Role option for temporary key generation.
When Role ARN is specified on the record, use out of the box AWS STS Assume Role task to generate temporary credentials with permissions restricted by the specified role.
- Field Type: String
- Name: RoleARN
- Display Name: Role ARN
- Order: 300
STS Endpoint can be added to the record type to overwrite the system default value of sts.amazonaws.com.
Providing the ability for user’s to enter another STS endpoint introduces support for multiple regions.
- Field Type: String
- Name: STSEndpoint
- Display Name: STS Endpoint
- Order: 400
STS Region can be added to the record type to overwrite the system default value of us-east-1 as the region.
- Field Type: String
- Name: STSRegion
- Display Name: STS Region
- Order: 500
You may also define these values globally in the PAM system configuration ($PAM_HOME/web/conf/catalina.properties).
Add these lines as needed, save the file and restart the PamManagement/pammanager service to complete the configuration:
xtam.aws.sts.endpoint=<your STS endpoint>
xtam.aws.sts.region=<your STS region>