Updating Original PAM Deployment to Latest Framework and WEB Container
This guide is designed for original PAM deployments that wish to update to the latest Framework and WEB Container components.
To verify if this guide is applicable to your PAM deployment, navigate to Management > About and check both the Framework and WEB Container versions.
If the Framework version begins with 1.8x and the WEB Container begins with 8.0.x, then this guide can be used to update your PAM deployment to the latest supported versions.
If the Framework version begins with 11.x or higher, then please use this guide to update the Framework.
If the WEB Container version begins with 9.0.x, then please use this guide to update the WEB Container.
Prerequisites
- An operational PAM deployment with the latest version. Please update to the latest available version before proceeding.
Considerations
- Each PAM node that is updated will be offline and inaccessible for the entirety of the migration.
- The user performing the migration will be required to update files and configurations on the PAM host server. Appropriate privileges are required.
- We highly recommend deploying a test instance of PAM that mirrors your production instance as closely as possible to test the migration (DB type, Federated Sign-In, certificates, MFA/SSO, AD Integration, etc). Once the migration is successful with the test instance you can reproduce the procedure on your production instance.
Please read the entire procedure outlined in the article before beginning. If you have any questions, please contact the Support team: https://support.imprivata.com/.
Step 1. Download Migration Components
- Download the latest framework packaged for PAM Server using the appropriate links below to your PAM host server and extract archive outside the $PAM directory.
-
Download the latest WEB Container packaged for PAM Server to your PAM host server and extract archive outside the $PAM_HOME directory.
- Windows and Linux: https://bin.xtontech.com/product/pam-web.zip
-
Download the OpenJDK 11+ compatible PAM Federated Sign-in Module from the below location. Please note that if you are not using the Federated Sign-in Module, then you can skip this step.
-
Download the JDK Update Pack to your PAM host server (Windows and Linux) and extract the archive to your $PAM_HOME directory. The extracted archive will create a new directory with the name $PAM_HOME/pam-jdk13-pack.
Step 2. Stop the PAM Services
Once the services are stopped, PAM will become inaccessible until the entire migration is completed.
- For Windows deployments, stop the PamManagement and PamDirectory services: Copy
net stop PamManagementCopynet stop PamDirectory
-
For Linux deployments, stop the pammanager and pamdirectory services:
Copyservice pammanager stopCopyservice pamdirectory stop
Step 3. Updating Framework and WEB Container Version
- Replace the existing PAM jre directory.
Rename $PAM_HOME/jre to $PAM_HOME/jre.old folder
Move jre directory downloaded in the Step 1a to $PAM_HOME/jre
-
Copy existing PAM Certificates and Configurations:
-
Copy the file $PAM_HOME/jre.old/lib/security/cacerts to $PAM_HOME/jre/lib/security overwriting the current file.
-
-
Update WEB Container:
-
Copy existing $PAM_HOME/web directory to the $PAM_HOME/web.old to create a backup.
-
Copy all files from the directory web/bin downloaded in the Step 1b to $PAM_HOME/web/bin,
-
Copy all files from the directory web/lib downloaded in the Step 1b to $PAM_HOME/web/lib.
-
-
Update PAM container files. This step should be performed for existing deployments that were done before March, 2019. All deployments performed after March, 2019 already include modifications in these files.
-
Copy all files from $PAM_HOME/pam-jdk13-pack/bin to $PAM_HOME/bin overwriting the current files.
Note: This step resolves two issues with the compatibility between Java versions: deprecated endorsed folder and endpoint identity verification for LDAPS integrations.
-
-
(Windows only) Redeploy Service. This step should be performed for existing deployments that were done before March, 2019. All deployments performed after March, 2019 already include these modifications.
-
Redeploy the Federated Sign-In Module. If you are not using the Federated Sign-in Module, you can skip this step. This step should be performed for existing deployments that were done before March, 2019. All deployments performed after March, 2019 already include modifications in these files.
-
Copy the downloaded cas.war from step (1c) to $PAM_HOME/web/webapps.
Note: If you made any customizations to the Federated Sign-in Module, they may be lost and need to be redone after the migration is complete.
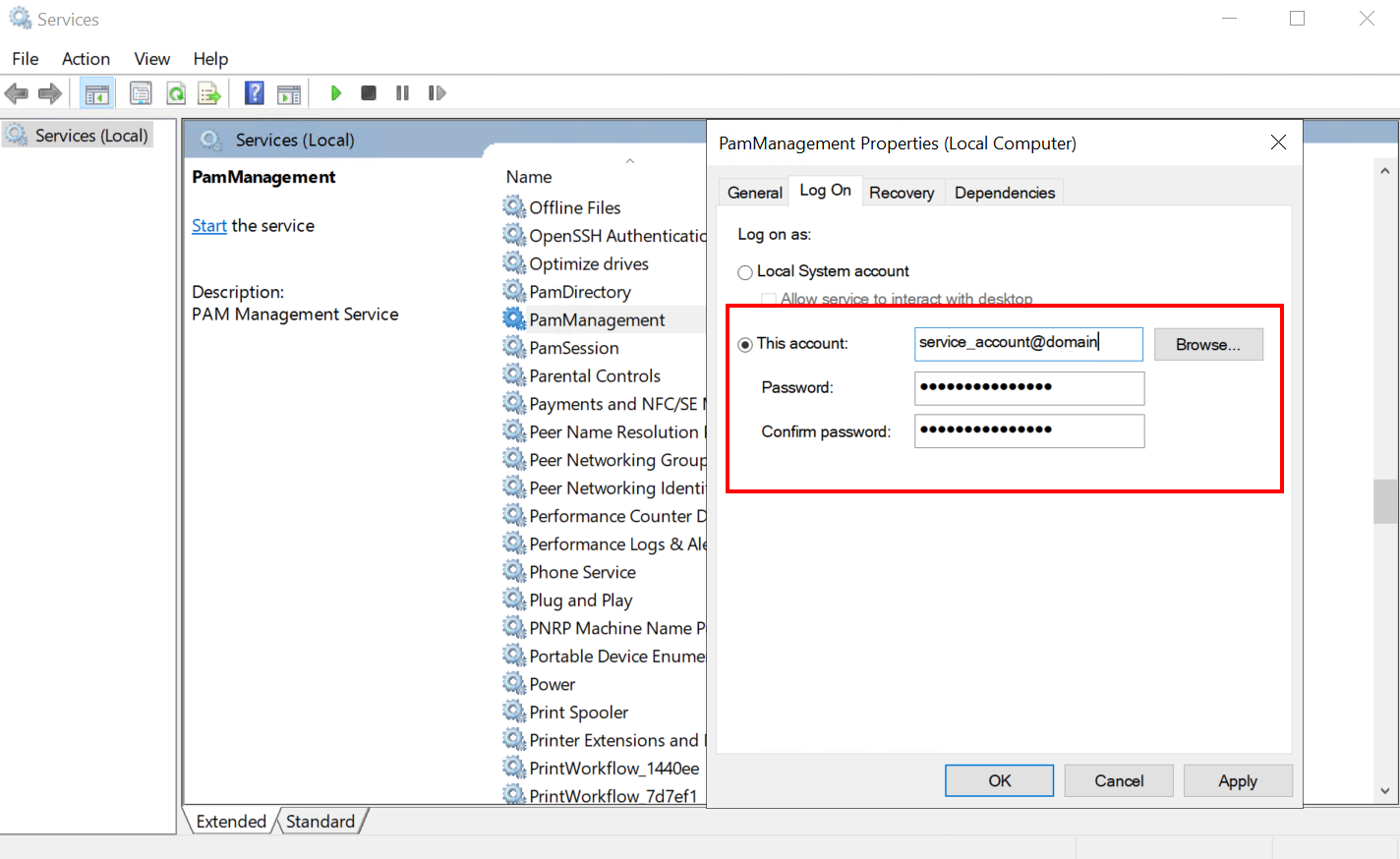
Note: The PamManagement service resets to the default Local System account Log on property once this service for PAM is reinstalled. If you are using a Log account other than an Local System account for this service then you must restore it prior to restarting the PamManagement service. Navigate to Services on Windows and find PamManagement, right-click and select Properties. Go to the Log on tab, select This account: and restore the required service account.
-
Note: This step will migrate the existing certificates loaded into the previous PAM deployment including ADS, AD connection certificates as well as SSL certificate for CAS integration.
Step 4. Start the PAM Services
- For Windows deployments, start the PamManagement and PamDirectory services:
-
For Linux deployments, start the pammanager and pamdirectory services:
Copyservice pamdirectory startCopyservice pammanager start
net start PamDirectory
net start PamManagementStep 5. Test and Verify
Once the services come back online, you should now login and thoroughly test the system.
This should include, but not be limited to:
- Login with all applicable types of user accounts; Local, AD/LDAP, MFA and SSO.
- Accessing existing records (and creating new records) in both the Record List and Personal Vault, including the unlock action.
- Creating remote sessions.
- Executing jobs and tasks (on demand and scheduled).
- Viewing and exporting reports.
To confirm the migration, check Framework and WEB Container versions on the bottom of Administration / Settings / Database screen.
The displayed versions should match version that was downloaded.
Rollback
If the migration or testing fails and you need to roll back to the previous Java framework and a WEB Container, then follow this procedure. If you do not need to rollback, proceed to the next section.
- Stop the PAM services as described earlier
- Rename the new $PAM_HOME/jre to $PAM_HOME/jre.new
- Rename the previous $PAM_HOME/jre.old back to $PAM_HOME/jre
- Rename the new $PAM_HOME/web to $PAM_HOME/web.new
- Rename the previous $PAM_HOME/web.old back to $PAM_HOME/web
- Start the PAM services as described earlier.
When the services come back online, PAM should be using the previous framework.
You should now perform the testing and validation again.
Step 6. Cleanup
After all the testing is complete and the system is fully operational, you may remove the following directories:
- $PAM_HOME/jre.old
- $PAM_HOME/web.old
- $PAM_HOME/pam-jdk13-pack
- Files downloaded in Step 1 and extracted archives.