Generate and Replace the SSL Certificate for PAM Local Directory Service
Use this guide to generate a new SSL certificate for use by PAM’s Local Directory Service and to replace the existing certificate.
-
Generate a new certificate by executing the following command from the command line in the PAM home folder $PAM_HOME:
-
Edit the Apache DS LDAP settings file ads-serverid=ldapserver.ldif located in the following folder using a text editor:
CopyOn a Linux host:
$PAM_HOME/ds/instances/default/conf/ou=config/ads-directoryserviceid=default/ou=serversCopyOn a Windows host:
$PAM_HOME\ds\instances\default\conf\ou=config\ads-directoryserviceid=default\ou=serversAdd 2 new parameters to the end of this file with the path to the keystore file and its password:
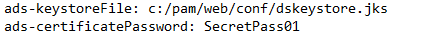
ads-keystoreFile:
ads-certificatePassword:
Password can be stored as plain text or base64 encoded string. If you are using the base64 variant you'll need to add a second colon after the parameter name as shown in the second example below.
The plain text version will look similar to this:
And base64 encoded:

You can convert a plain text to base64 using an online service or OS command-line utility: https://www.base64encode.org
-
Restart the PamDirectory or pamdirectory service.
-
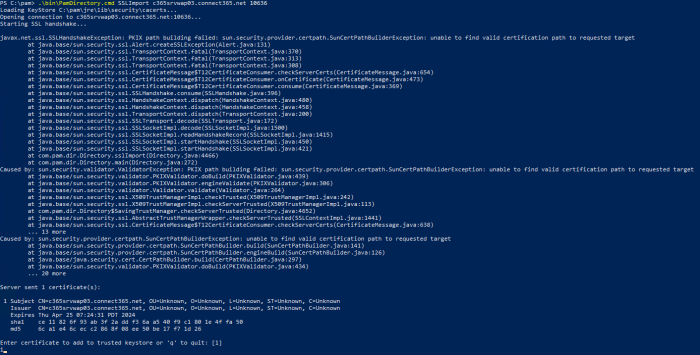
On all master nodes run the following command from the $PAM_HOME location to import the new certificate:
-
Add the certificate to the java cert store by choosing 1 in the dialog
-
Restart pammanager (Linux) / PamManagement (Windows) service on master nodes.
bin/PamKeytool.sh -genkey -keyalg "RSA" -alias ads.local -keystore web/conf/dskeystore.jks -validity 730 -deststoretype jks
bin\PamKeytool.cmd -genkey -keyalg "RSA" -alias ads.local -keystore web\conf\dskeystore.jks -validity 730 -deststoretype jks
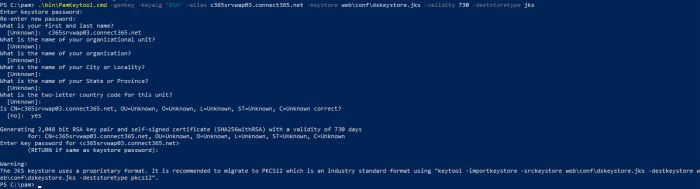
Please note that the only field you have to fill is "What is your first and last name?” For this field, enter the FQDN which you'll use to connect from other nodes, or the host name of this node itself.