AD Authentication is Slow
Active Directory User Authentication to the PAM is slow. What causes this and how can it be improved?
System caches AD group membership by user after their initial login for a period of one day because this is usually the slowest operation for validating permissions (the one that contributes to the slow initial load).
System cleans its cache after the user logouts or when an PAM System Administration presses Reset Cache button on the Administration > Settings > AD page.
There are several ways to optimize this initial query. All methods could be used simultaneously or just some of them depending on your requirements.
The first method
The first method is to limit the user and group locations to some branch of the AD forest.
Often, AD forests include very slow trusts that could be eliminated by restricting queries to certain branches where all System applicable users and groups are located.
In a default installation, PAM attempts to use the whole tree because it does not know where users and groups are coming from; however, it is possible to limit the branch for your production use.
To do this, use the following parameters in $PAM_HOME/web/conf/catalina.properties file to define certain org units or other branches of the forest:
ldap.rootDn=
ldap.baseDn=
ldap.roleBase=
For example, we can restrict queries to the following branch CN=Users,DC=contoso,DC=com as compared to the complete tree using only DC=contoso,DC=com.
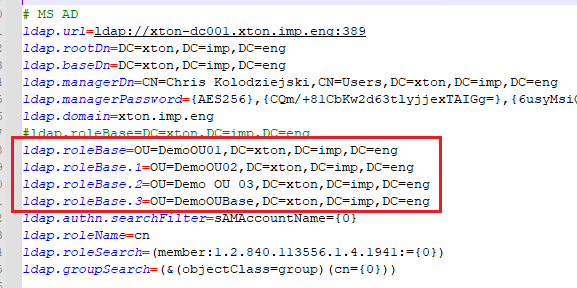
Note: ldap.roleBase must remain as a valid parameter as it does in our default configuration today. Additional ldap.roleBase parameters can be added, each with an increasing value beginning with .1.
ldap.roleBase=
ldap.roleBase.1=
ldap.roleBase.2=
ldap.roleBase.3=
etc
The second method
The second method is to not integrate directly with AD domain controller but rather with its AD Global Catalog which, when optimized, performs faster with complex queries.
The AD Global Catalog is usually accessible on the same domain controller for the forest over port 3268 or 3269 for LDAPS access.
The third method
The third method is to change the way PAM queries group membership for any specific user.
By default, it does one recursive query to Active Directory that returns all nested groups a user belongs to.
While some Domain Controllers are optimized well to execute queries like these, for some Active Directory servers this is very heavy operation.
In this case, it is more desirable for the AD client (like Privileged Access Management) to query groups one-by-one instead of relying on AD to execute a combined recursive query to return all groups. The switch is controlled by the parameter ldap.roleSearch in the $PAM_HOME/web/conf/catalina.properties file.
The following is the default value for this parameter (recursive query):
ldap.roleSearch=(member:1.2.840.113556.1.4.1941:={0})
To further narrow the search to only groups that are mapped to PAM , add the following property to in the $PAM_HOME/web/conf/catalina.properties file and specify the group names that are associated in PAM. PAM will then ignore all other groups and should help improve the Login experience.
This is only available in PAM version Release 2.3.202503301554 (March 30, 2025) or later:
ldap.pam.userGroupsList=(&(objectClass=group)(|(cn=group-001New)(cn=group-002New))(member:1.2.840.113556.1.4.1941:={0}))
To switch PAM to execute multiple queries for nested groups, change the parameter to this:
ldap.roleSearch=(member={0})
Afterwards, save and close the file and finally restart the PamManagement (Windows) or pammanger (Linux) service.
This parameter will instruct the System to execute a query to get all groups a user belongs to and then to execute the same query for each group returned to cover the case of nested AD groups.
We observed that some domain controllers perform faster using this method. Before doing this, you might want to test against your active directory server to determine which query is faster by using some common AD/LDAP query tool like ldapsearch, Softerra, Apache Directory Studio. Also, it is important to understand if your AD domain controller that can even execute queries like these before you make any changes.