Integration with WatchGuard AuthPoint
Configuration for PAM and WatchGuard AuthPoint MFA Integration
PAM supports integration with SAML providers like WatchGuard AuthPoint to allow their unique multi-factor authentication (MFA) solution to handle the second authentication method, enabling even greater security for your PAM deployment.
The following guide describes how to configure your PAM and WatchGuard AuthPoint integration.
Requirements
Before you begin your integration, be sure you meet the following pre-requisities:
- A working PAM deployment with the Federated Sign-In experience.
- Access to your existing PAM host server. You will need to update a configuration file, certificates and restart services.
- Access to your WatchGuard portal to configure your AuthPoint authentication services.
- If Users are created and managed in WatchGuard, then a matching user must also be created as an PAM Local User.
- If Users are synced from Active Directory to WatchGuard, then you must also integrate PAM with the same Active Directory.
Step 1: Begin the AuthPoint Configuration
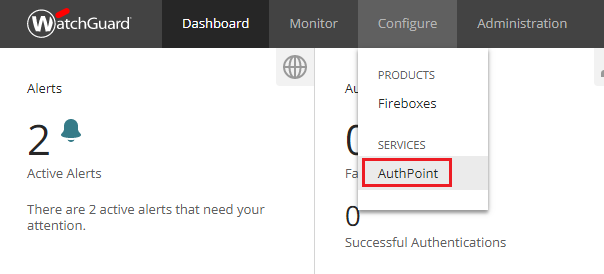
- Login to your WatchGuard portal. This guide is built using the WatchGuard Cloud portal as available in October 2019.
- Navigate to Configure > AuthPoint.
-
From the AuthPoint page, select the Resources option from the left navigation. From the Resources page, click the CERTIFICATE button to generate a certificate.
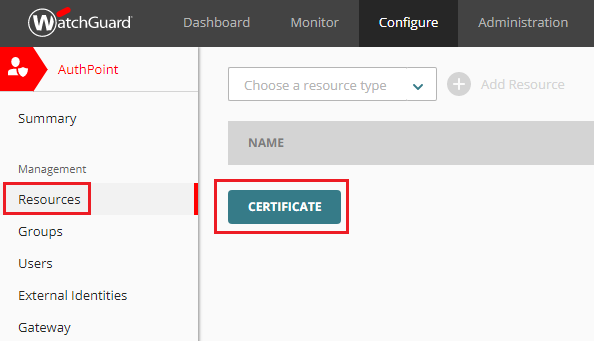
-
When the certificate appears, click the menu on the right (three dots) and use both the Download Certificate and Download Metadata files. Save both files to a safe location as they will be needed in a future step.
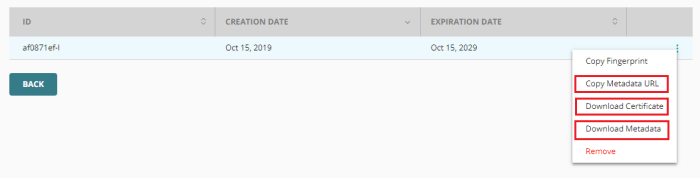
-
From the same menu (three dots), open the Copy Metadata URL option and save this URL. We will need this full URL in a future step.
Step 2: Perform the Configuration
- Login to your PAM host server.
- Move or copy both the downloaded Certificate and Metadata files from step 1.4 to the $PAM_HOME\content\keys directory.
- Import the AuthPoint certificate to the PAM keystore using the following procedure:
Open a prompt and navigate to the $PAM_HOME directory. You may need sudo or elevated permissions.
Execute the following command:
For Windows, confirm the name of the .cer file and its location to be imported and used by PAM:
Copybin\PamKeytool.cmd -import -alias xtauthpoint -file content\keys\wg-authpoint-saml-certificate-202910-base64.cer -keystore jre\lib\security\cacertsFor Unix or Linux, confirm the name of the .cer file and its location to be imported and used by PAM:
Copybin/PamKeytool.sh -import -alias xtauthpoint -file content/keys/wg-authpoint-saml-certificate-202910-base64.cer -keystore jre/libsecurity/cacertsAfter the command is issued, you will be prompted for the keystore password. Enter the value changeit and press the Enter key to continue.
When prompted Trust this certificate? enter y and press the Enter key. You will receive the message Certificate was added to keystore when it has imported successfully.
-
Open the file $PAM_HOME/web/conf/catalina.properties in a text editor and add the following new section. Confirm that the values for each parameter is accurate to your PAM deployment.
Copy#AutoPoint SSO SAML
cas.authn.pac4j.saml[0].clientName=AuthPoint
cas.authn.pac4j.saml[0].keystorePassword={password}
cas.authn.pac4j.saml[0].privateKeyPassword={password}
cas.authn.pac4j.saml[0].serviceProviderEntityId={managed_path}
cas.authn.pac4j.saml[0].serviceProviderMetadataPath={metadata.xml}
cas.authn.pac4j.saml[0].keystorePath={samlKeystoreAuthpoint.jks}
cas.authn.pac4j.saml[0].identityProviderMetadataPath={path}
cas.authn.pac4j.saml[0].maximumAuthenticationLifetime=2073600In the lines above, the following {placeholders} need to be updated using your own values explained here.
Save and close the file when you are finished.
-
cas.authn.pac4j.saml[0].keystorePassword={enterSomePassword} - Create an alphanumeric password. Any value you want to enter.
-
cas.authn.pac4j.saml[0].privateKeyPassword={enterSomePassword} - Create an alphanumeric password. Any value you want to enter.
-
cas.authn.pac4j.saml[0].serviceProviderEntityId={managed_path} - Replace this placeholder URL with your full https PAM login page URL ending with /xtam/, for example https://pam.yourorg.com/xtam/.
-
cas.authn.pac4j.saml[0].serviceProviderMetadataPath={$PAM_HOME/content/keys/metadata.xml} - The full path and file name of the authpoint.xml file that will be created after a PAM service restart later in this guide, the .xml file from step 1.4. For example, $PAM_HOMEcontent/keys/samlKeystoreAuthpoint.xml (use forward slashes not backslashes).
-
cas.authn.pac4j.saml[0].keystorePath={$PAM_HOME/content/keys/samlKeystoreAuthpoint.jks} - Define a path and name for the PAM auto-generated key that will be created after a PAM service restart later in this guide. For example, $PAM_HOME/content/keys/samlKeystoreAuthpoint.jks (use forward slashes not backslashes).
-
cas.authn.pac4j.saml[0].identityProviderMetadataPath={path} -This will be the full URL of the IDP Metadata URL from the AuthPoint Application temporarily saved to a file in the previous step 1.5.
Please note, if you made changes around SSO parameters to the $PAM_HOME/web/conf/catalina.properties file with the previously generated .xml and .jks files, you need to regenerate those files to apply the new changes.
-
-
When complete, save and close your catalina.properties file.
-
Restart the PamManagement (Windows) or pammanager (Linux) service. After the service fully restarts, it could take 3-5 minutes to fully restart, the keystore file should appear in $PAM_HOME/content/keys/samlKeystoreAuthpoint.jks or the location you defined in the catalina file.
-
Next, we will export the SAML certificate from PAM using the following procedure.
-
Open or reuse your existing prompt and navigate to the $PAM_HOME directory. You may need sudo or elevated permissions.
-
Execute the following command:
For Windows:
Copybin\PamKeytool.cmd -keystore content\keys\samlKeystoreAdfs.jks -export -alias saml2clientconfiguration -file content\keys\adfsxtam.cerFor Unix or Linux:
Copybin/PamKeytool.sh -keystore content/keys/samlKeystoreAdfs.jks -export -alias saml2clientconfiguration -file content/keys/adfsxtam.cer
-
-
Now we need to convert your exported certificate file to base-64 encoding. Use whatever method you are most comfortable with. In Windows, we believe the easiest method is the following:
-
Double click on your certificate file and click Open if you receive a security prompt.
-
From the Certificate dialog, switch to the Details tab and click the Copy to File... button.
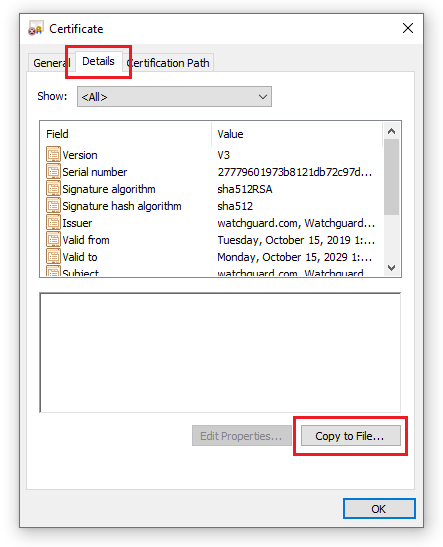
-
On the Certificate Export Wizard screen, select the format Base-64 encoded X.509 (.CER) option.
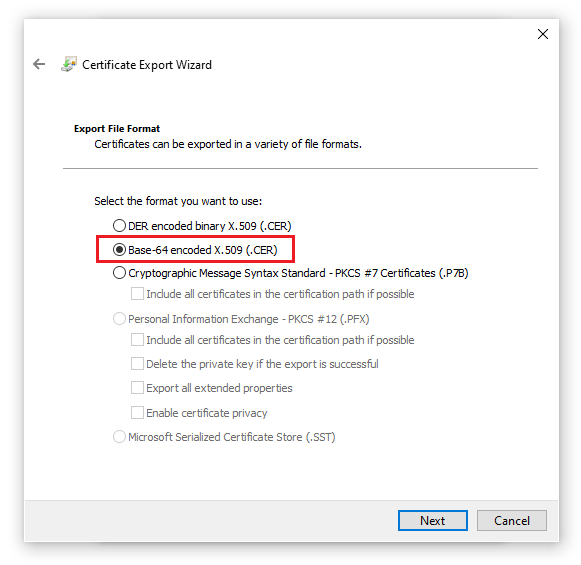
-
Save this converted certificate file to $PAM_HOME/content/keys.
-
Step 3: Complete the AuthPoint Configuration
- Return to your WatchGuard portal.
- From AuthPoint’s Resources page, expand the Choose a resource type dropdown menu, select the option SAML and finally click Add Resource.
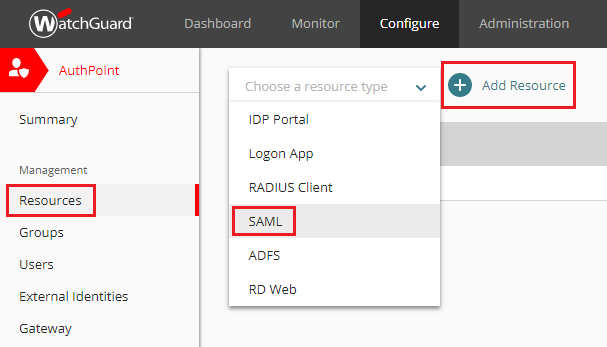
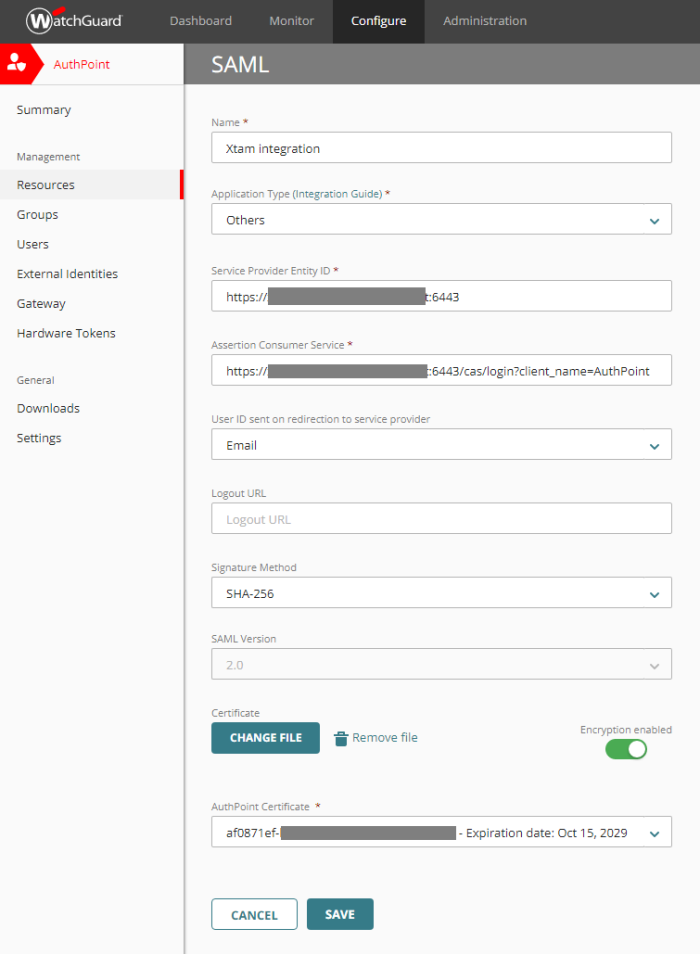
- Enter values for all necessary fields that match those that were entered into the catalina.properties file from the previous step.
-
Name: Enter a meaningful name
Application Type: Others
Service Provider Entity ID: {managed_path value from step 2.4}
Assertion Consumer Service: {managed_path value from step 2.4}/cas/login?client_name=AuthPoint
User ID sent on redirection to service provider: Email
Logout URL: empty
Signature Method: SHA-256
For the Certificate, click the CHOOSE FILE button and select your converted base-64 encoded certificate file from the previous step. - Click the slider so that Encryption enabled is turned on.
- Click the SAVE button to complete the resource creation.
- Next, navigate to the AuthPoint’s Groups page and click the Add Group button.
-
Enter a meaningful Name (required) for this new Group and a description (optional).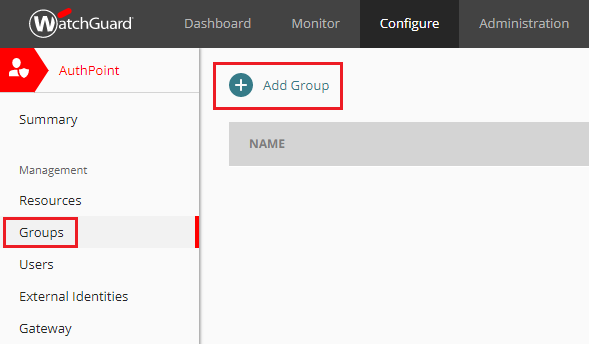
-
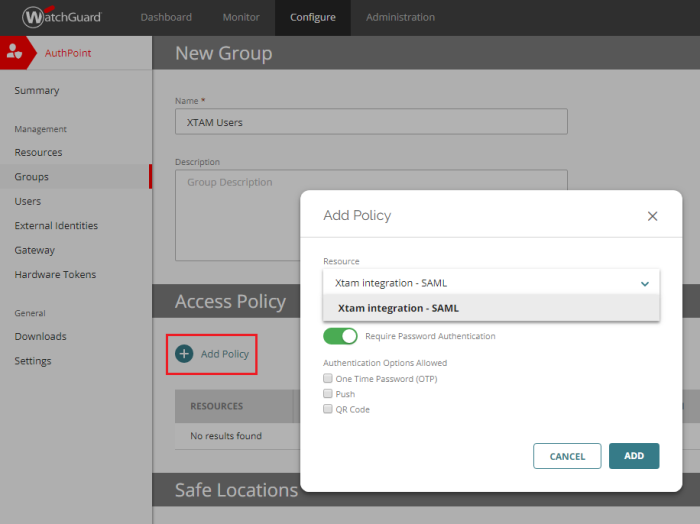
Now for this Group, click the Add Policy button, select the Resource we created in the previous step from the dropdown and finally configure your security policies as desired. Click ADD to complete the creation of your policy.
-
Next, navigate to the AuthPoint’s Users page and click the Add User button.
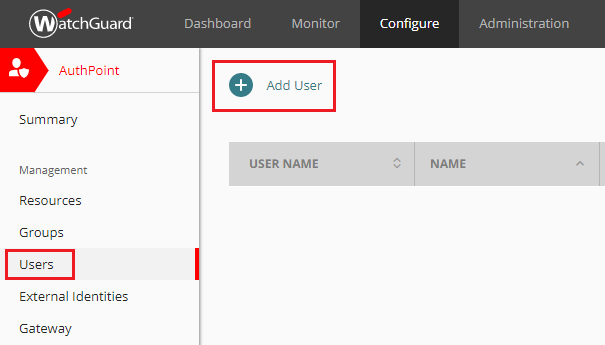
-
Fill out all required fields as needed for this new User. For the Group parameter, select the Group that was created in the previous step. Click the SAVE button to create this new user.
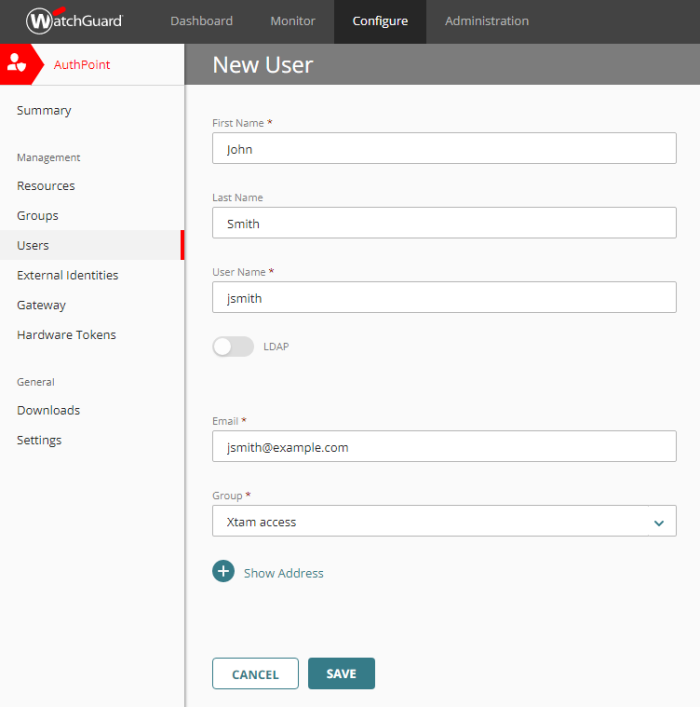
-
Finally, you can open your PAM login page, click the red button named AuthPoint and test the login process with the User that was created in the previous step. Remember that an identical User account must also be created on PAM’s Local Users page.
To regenerate .xml and .jks files
-
On the PAM host computer, open the following file in a text editor $PAM_HOME/web/conf/catalina.properties locate the section labeled # CAS and specify the stated location for those files.
-
Remove or delete these previously generated .xml and .jks files from the location.
-
Restart PamManagement (Windows) / pammanager (Linux/Unix) service to regenerate those two .xml and .jks files, so your changes around SSO parameters can apply back to PAM.