Integration with YubiKey
If you are already a user of YubiKey Multi-factor or Two-factor authentication and would like to configure PAM to use YubiKey, then please perform the following steps.
Please note that you will need to be able to access and modify files on PAM host computer. Contact your System Administrator for assistance.
Pre-requisite: PAM must be deployed with and configured to use its Federated Sign-In component in order to integrate with multi-factor authentication providers. For YubiKey MFA Integration, download this Federated Sign-in Module and follow the guide linked above for configuration.
Step 1. Register your YubiKey to get Yubico API Keys
Step 2. Configure Integration with YubiKey
Step 1. Register your YubiKey to get Yubico API Keys
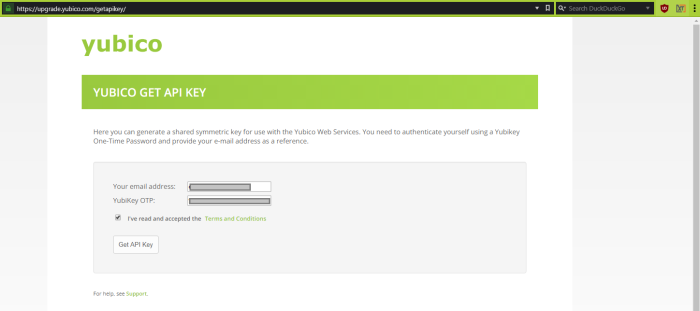
- Open your browser to https://upgrade.yubico.com/getapikey/
- Enter your email address into the required field.
- Enter your key’s OTP or touch your YubiKey to populate the YubiKey OTP field.
- Check the box to accept the Yubico Terms and Conditions.
- Click the Get API Key button.
-
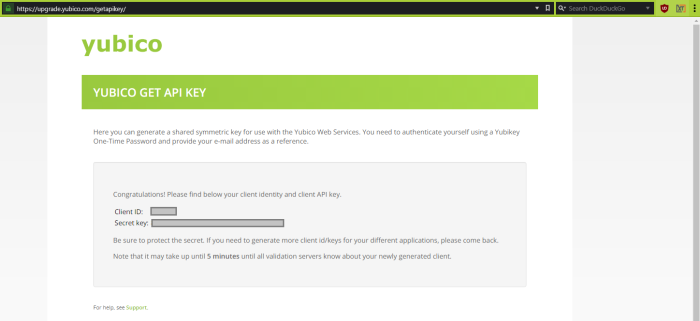
The Yubico website will now display your client identity and client API keys. Save this information to a safe location or do not close your web browser. You will need both the Client ID and Secret key values in the next step.
Step 2. Configure Integration with YubiKey
- Log on to PAM host computer.
- Open the file $PAM_HOME/web/conf/catalina.properties in a text editor.
- In this file, scroll down to the section labeled # YubiKey. If you do not have this section, copy and paste the entire section below to the bottom of your file.
- Uncomment the following line only when a single global MFA for the entire PAM is desired:
-
Add your Client ID and Secret Key from Step 1 to the following lines:
Copycas.authn.mfa.yubikey.clientId=clientID
cas.authn.mfa.yubikey.secretKey=SecretKey -
If you are using your own Database and not the PAM internal database, then modify the following lines. If you are using PAM’s internal database, then skip this step.
Copycas.authn.mfa.gauth.jpa.database.driverClass=org.apache.derby.jdbc.ClientDriver
cas.authn.mfa.gauth.jpa.database.dialect=org.hibernate.dialect.DerbyTenSevenDialect - You can find the values that need to be replaced in bold above from this same /catalina.properties file in the #PAM Database section. In this example, we would copy the bolded SQL database parameters below and use them to replace those of the Derby database above.
-
When complete, save and close this file.
-
Restart the service PamManagement (Windows) or pammanger (Linux).
# YubiKey
# Get your API clientId and secretKey here: https://upgrade.yubico.com/getapikey/
#cas.authn.mfa.globalProviderId=mfa-yubikey
cas.authn.mfa.yubikey.clientId=clientID
cas.authn.mfa.yubikey.secretKey=SecretKey
cas.authn.mfa.yubikey.name=PAMYubiKey
cas.authn.mfa.yubikey.jpa.dataSourceName=java:comp/env/jdbc/PamDB
cas.authn.mfa.yubikey.jpa.driverClass=org.apache.derby.jdbc.ClientDriver
cas.authn.mfa.yubikey.jpa.dialect=org.hibernate.dialect.DerbyTenSevenDialect
cas.authn.mfa.yubikey.jpa.dataSourceProxy=true
cas.authn.mfa.yubikey.jpa.ddlAuto=update
#cas.authn.mfa.globalProviderId=mfa-yubikeyIf you wish to enable different MFA providers for individual users or group, please read this article for additional information.
hibernate.dialect=org.hibernate.dialect.SQLServer2012Dialect
hibernate.connection.driver_class=com.microsoft.sqlserver.jdbc.SQLServerDriverThis configuration will enable YubiKey as the global MFA provider in the System for all user logins. YubiKey MFA supports connection for users who using native clients such as PuTTY, mstsc, MobaXTerm, Secure CRT, Royal TS, WinSCP, scp, etc via SSH Proxy or RDP Proxy. If you wish to configure additional MFA providers or to enable YubiKey only for selected users or groups, then please see our MFA Configuration Guide article for more information.
Once configured, refer to the following article YubiKey – How to Login as a User for steps on how to use YubiKey MFA with the System from an end user’s perspectives.