Appendix
Remote Session Manager Configuration
When installing the Session Manager component on a remote Unix or Linux computer(s), then the following steps should be taken.
-
Ensure that PAM is Installed and configured on your master computer.
-
Run the install script on the remote computer where Session Manager is to be deployed.
-
Read and accept the License Agreement by pressing <ENTER> to display the agreement, <Q> when finished and finally <Y> to accept it and continue.
-
Enter <N> to exclude each component except for the “Session Manager component” which you will include <Y>.
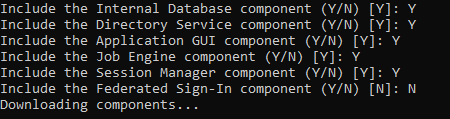
Select the "Session Manager" component
-
Next, enter the location of the certificate bundle that was deployed to your master computer where PAM was installed earlier and press <ENTER> to continue.
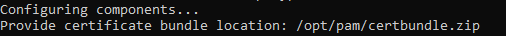
Enter the Certificate Bundle file location
-
The certificate bundle is in the root PAM installation directory on your master computer. The default file location is /certbundle.zip
-
You may select the zip file from this default location (if possible), copy it to a shared network location or simply copy the zip file to this remote computer and select it locally.
NOTE: This step is optional, so if you wish to not supply the certificate you may simply click Next to continue. By skipping this option, you are acknowledging that the communication between PAM on the master computer and this remote Session Manager computer will not be secured. Because of this, it is recommended that you supply the certificate when prompted and do not skip this step.
-
The Session Manager service will now startup on this computer and the installation script will finalize the operation.
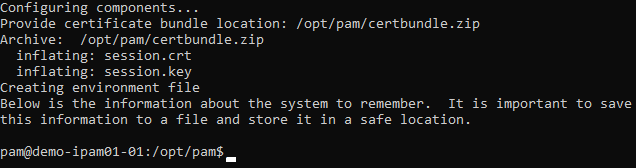
Session Manager Component Deployed
Web Server
If you are configuring PAM using a trusted SSL certificate or exposing it to external traffic, then a web server will need to be deployed and configured.
The PAM installation process does not include web server deployment and configuration and therefore should be performed by a knowledgeable Unix administration.
Popular web servers include Apache HTTP or NGINX.
The purpose of the web server is to act as a reverse proxy.
Its forwarding rules should process the certificate secured HTTPS 443 inbound port and route it to the PAM port (default 8080) inside the server.
Since the trusted SSL certificate is applied to a specific domain (i.e. https://host.example.com) this URL becomes the managed path for PAM’s Federated Sign-In server.