Just-In-Time Permission Elevation
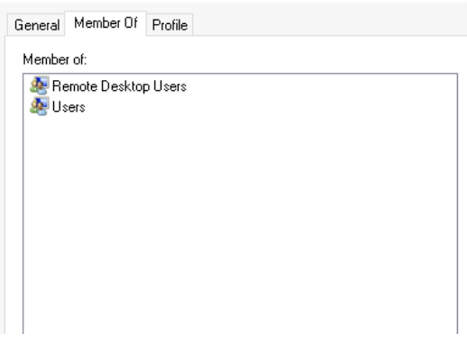
A Just-In-Time Permission Elevation option is designed to promote increased security using the principle of no standing trust.
This design also limits the time a privileged account exists on a critical system, especially with enabled special access.
The goal is not just about limiting time, but to have a zero standing privilege strategy on users and servers.
Just-In-Time (JIT) Permission Elevation helps customers implement these strategies and reduce the number of privileged accounts in their network and control access to active privileged accounts.
Prerequisites:
Just-In-Time Permission Elevation is supported ONLY for Windows Hosts.
Create Just-In-Time Permission Elevation Record Type
Step 1. Create a new PAM record
-
Login to PAM as a System Administrator.
-
Navigate to Administration > Record Types.
-
Click on the New Record Type button.
-
Enter a unique name for this new record type, select in the first field: Session Manager > RDP. Leave the second field Hidden Field unchecked (blank).
-
Click Save in the top right corner.
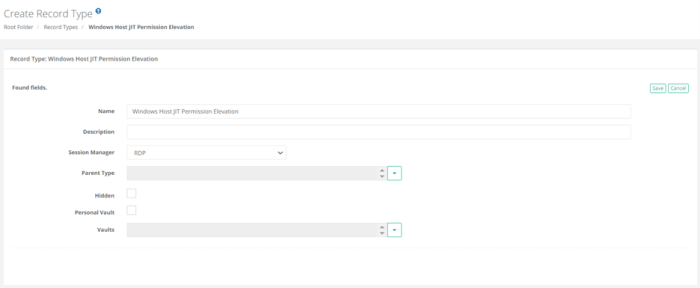
Step 2. Add Just-In-Time (JIT) Record type
The fields of this Just-In-Time (JIT) Record type will need to be added.
-
Click the Add Field button towards the bottom of this page and add the minimum required fields: Host, Port, User and Password.
If other fields for the Just-In-Time (JIT) record type are required per your configuration, please also add those fields as well during this step.
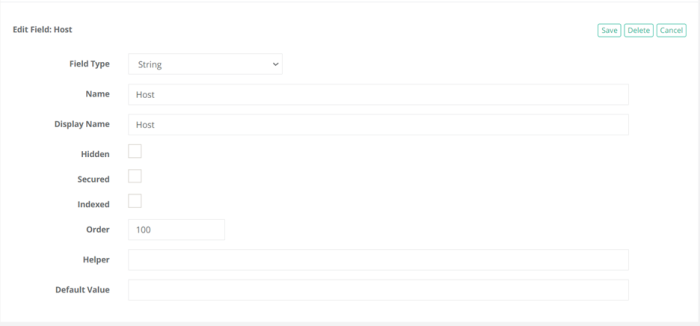
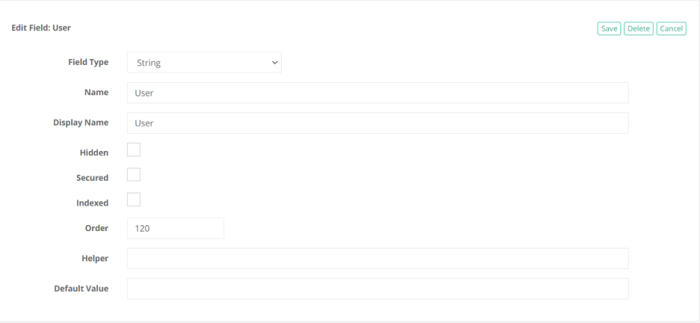
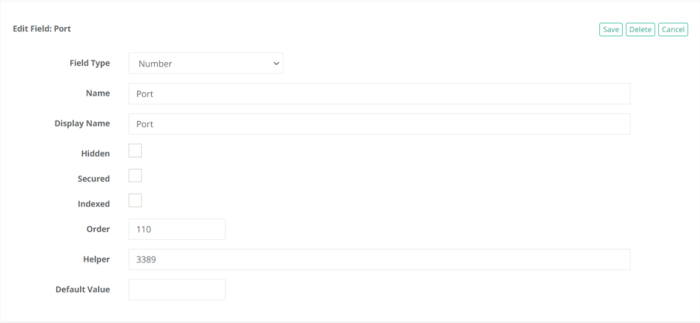
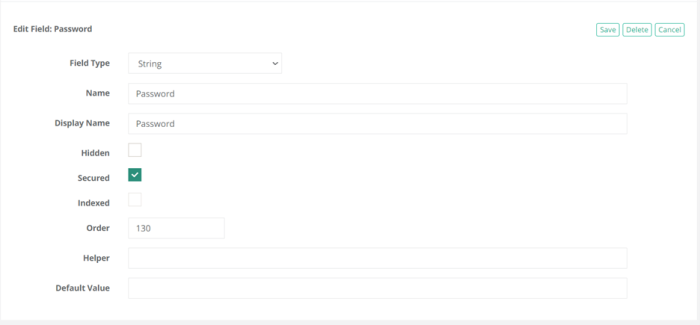
As a minimum requirement now the record type should look as below: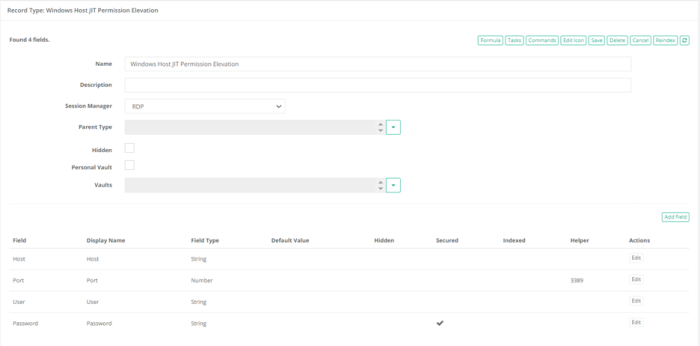
Step 3. Add Tasks
-
Next, click on the Tasks button to add the required tasks to perform the Permission Elevation against the host.
-
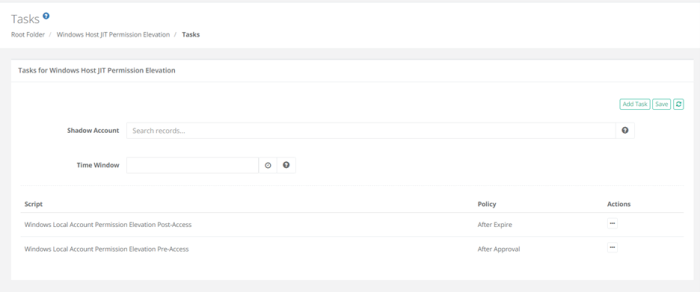
Click Add Task and add the following tasks:
-
Script: Windows Local Account Permission Elevation Post-Access with Policy: After Expire
-
Script: Windows Local Account Permission Elevation Pre-Access with Policy: After Approval
-
-
Once added the tasks page should now be set as shown below:
Step 4. Create your record
-
Navigate to a location in the Records vault where you wish to create the record and select Add Record > Windows Host JIT Permission Elevation.
-
Use this guidance to create your record:
Name enter a name for your record Description *optionally, enter a description for your record Host enter the host for the endpoint where the Permission Elevation will be required Port enter the port that will be used for connectivity User enter the username that will get Permissions Elevated Password enter the password of the user -
Click Save and Return.
Step 5. Configure the Task
Configure the Task that performs the Permission Elevation process.
-
In your new created record, click Manage > Tasks.
-
For the Shadow Account, select an existing record that contains the credentials of an account that can assign and remove user roles on this endpoint.
For example, in a Windows domain, this could be a record that contains the credentials of a Domain Administrator account.
-
read-only: if the Shadow Account field is read-only, that means it is set to inherit this Shadow Account from the record type. In this situation, you will need to navigate to Administrator > Record Types and add this Shadow Account directly to the Tasks list of this type. This will require your System Administrator account again. Alternatively, you can click the Make Unique button to break inheritance from the Record Type.
-
read/write: if the Shadow Account field is read/write enabled, then enter the name of the record that contains the credentials of an account that can create local accounts on this endpoint.
-
Once you have the Shadow Account configured, save your change and return to the record.
Step 6. Configure the Workflow
Next, configure the Workflow, whose approval and subsequent expiration, will trigger the creation and ultimate removal of the Permission Elevation.
Here is the help article about Workflows as well as a table of contents on the right-hand side about other Workflow related knowledge articles.
-
In the Record field select Manage > Workflows to configure a Workflow binding.
-
On the Workflow Bindings page, you will create a new Workflow binding that will be used to request access and once approved, the permission of the user in the record will get elevated to Administrator on the end point host.
-
Create the Workflow Binding as needed and click the Save button to complete the process. The required minimum of Workflow configuration for Just-In-Time Permission Elevation:
-
Actions
-
Time selectors

-
-
That completes the configuration of the Just-In-Time Permission Elevation process.
In the next section, we will illustrate the User experience from Workflow request through the Workflow expiration when the Permission Elevation is removed from the host.
The Just-In-Time Permission Elevation Process
-
Login to PAM with the user account that was bound by the Workflow created in the previous section.
-
Navigate to this Just-In-Time Permission Elevation record and click the Request Connect button.
-
Fill out the request access form as required and submit it when completed.
During testing, we would recommend requesting a short amount of time (i.e. 5 minutes) so that you do not have to wait too long for the workflow to eventually expire.
-
If the submitted workflow was not configured for automatic approval, Approve the submitted request to continue.
-
Once approved, PAM will begin the Permission Elevation process. Depending on the PAM queue, this process may take a few seconds or a few minutes to complete. You can follow the process by monitoring the Job History tab of this record.
-
After the Permission Elevation is successfully completed, the user’s Connect Requested button will change to Connect indicating that the user may now connect to the Host with the Permission Elevation as an Administrator on the host.
-
Click Connect to create your remote session. The User on the Record which is used to connect to the host is now an Administrator.
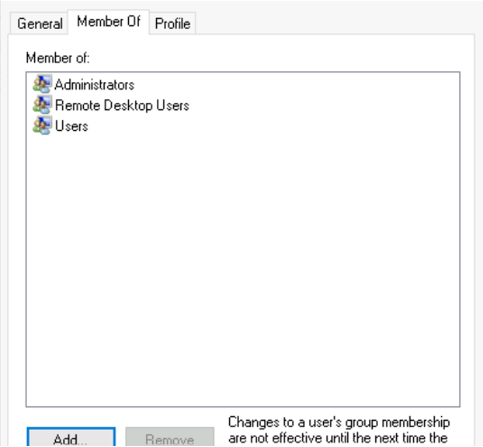
-
Finally, after the Workflow’s approved time expires PAM will execute the task to remove the Permission Elevation of Record User. The PAM user’s Connect button will change back to Request Connect and the Permission Elevation on the host will be removed.