RDP Client Proxy Sessions
Privileged Access Management (PAM) can create quick, easy and secure native client high-trust logins using your own desktop or mobile RDP client like Windows RDP client (MSTSC), Mac RDP client, Remote Desktop Connection Manager and mRemote while enforcing audit events, notifications, permissions, access request and password rotation.
Unlike other products, the PAM RDP Proxy provides this without having to download, install or maintain any custom launchers, agents or deployment packages to your computer or device.
Now your privileged users can securely connect to your managed Windows endpoints over RDP without disclosing passwords:
- Using their native Web browser (desktop or mobile) without installing any custom launchers, agents or packages.
- Using their native RDP client (desktop or mobile) without installing any custom launchers, agents or packages.
Secured passwords are never sent or synced to the user’s computer or mobile device. PAM maintains complete and total control of all passwords while the user connects to the managed endpoint and it can even reset the password after the user’s session has completed.
To learn about how PAM can provide secure SSH Proxy access using native SSH clients, please read our SSH client article.
The following sections describe how to create secure Windows Host RDP records in PAM and then how to use these records in your native desktop or mobile clients.
Enabling RDP Proxy
- Login to PAM with a System Administrator account.
- Navigate to Administration > Setting > Parameters.
- Locate and modify the following settings:
RDP Proxy: Switch this option to Enabled and click the Save button to its right;
RDP Proxy Port: Use or change the port value that the System will use for RDP proxy and click the Save button to its right.

-
Once both settings have been updated and saved, restart the PamManagement service (Windows) or pammanager service (Unix/Linux).
-
When the services is fully restarted (can take 1-5 minutes), the RDP proxy module is online.
Session record
Creating a RDP session record in PAM:
- In PAM, navigate to a Vault or Container and create a new record using the Windows Host record type.
- Populate all the fields with your endpoint’s connection details.
- Click the Save and Return button.
Your record is now saved and under management in PAM.
All access to this record will be captured in the audit log, including Active and Completed sessions.
Permissions and workflows can also be applied to your users or groups ensuring that only authorized personnel have access to the record.
RDP session record in a native Client
Use your RDP session record in a native RDP Client.
You can create your remote session in your native RDP client using one of two methods.
The first method is to populate your connection parameters into the client manually and the second method is to download a remote desktop file that already contains your Host and User values.
If you choose to download the remote desktop file, then you can skip to step 5 in this section.
Please note that for MFA authentication, your User value will need to be updated to contain the MFA token or MFA type as described below.
- If you are currently logged into PAM, please logout and log back in to the web portal. Any users that wish to connect using the RDP Proxy must sign in to PAM web portal once so their account can be automatically registered for this feature. They only need to do this login once, not every time thay wish to connect with the RDP Proxy.
- Open your local RDP client (we will use the native Windows 10 RDP client in our example but most other RDP clients function similarly) and create a new session.
- In the Computer field, enter the hostname of your PAM server followed by the configured RDP proxy port. For example, xtam.company.com:3388.
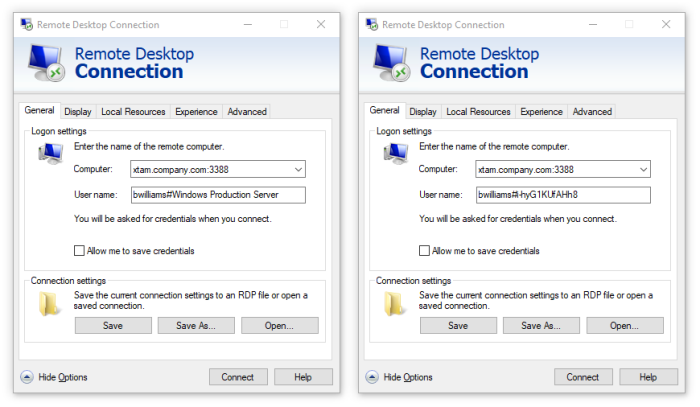
- In the User name field, enter a user string as described below:
- For TOTP like Google Authenticator or RADIUS like RSA, the Username string will follow this pattern:
- For Duo Security, the Username string will follow this pattern:
- Now, click the Connect button in your client.
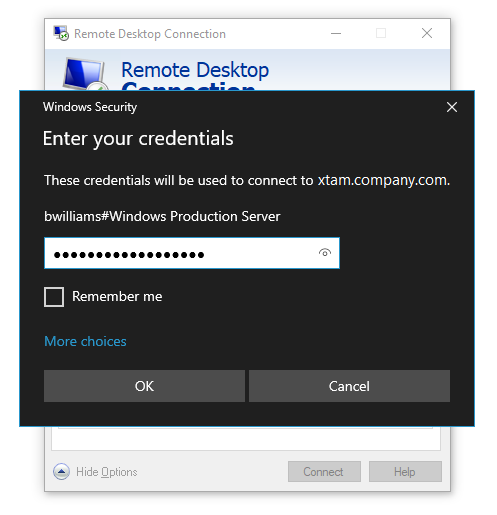
Enter the password for your PAM user account when prompted and click OK.
Note that you will be connecting to the PAM server rather than directly to this Windows endpoint.
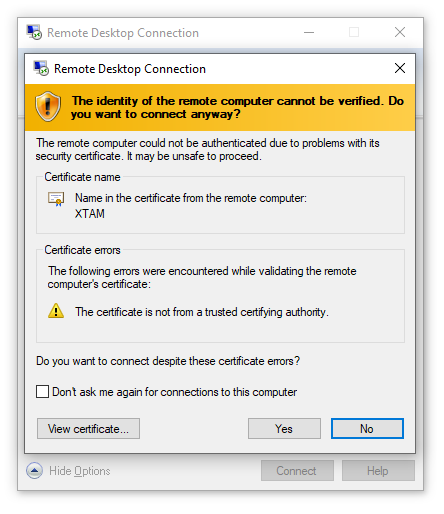
Confirm the PAM security certificate by clicking the Yes button.
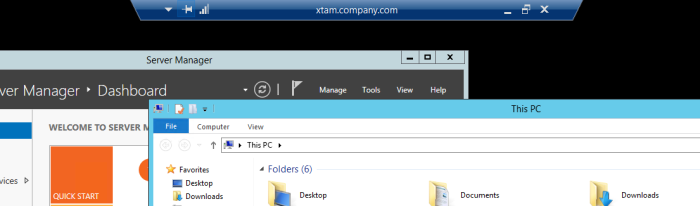
After a few moments, you will be connected to the remote RDP endpoint using the secured connection details in the referenced PAM record.
To confirm that the session is being provided via PAM, you can navigate to the Session tab of this record and note that there is now an Active session using this record. When you end the session using the native Disconnect or Sign Out options, the session will be reported as Completed.
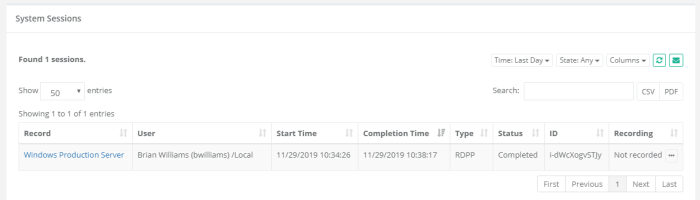
YourPAMLoginName#PAMrecordName or YourPAMLoginName#PAMrecordID
For example, if your login to the System was the username bwilliams and PAM record that contains the Windows Host RDP details has the name Windows Production Server and ID i-hyG1KUfAHh8, then the login string would be
bwilliams#Windows Production Server or bwilliams#i-hyG1KUfAHh8
When using the record Name to define the connection string, the record Name must be unique in PAM. If the name is not unique, the connection will fail and you must use its record ID instead.
A # (hash), % (percent) or : (colon) character may be used as a separate between the login and recordID values.The record’s ID can be found in the records’s URL or when viewing the record’s Details (https://xtam.company.com/xtam/#/records/record_view/i-hyG1KUfAHh8/type).
For users that are required to authenticate using MFA, your connection string for the Username name needs to include your MFA token or type. Please use the following examples to illustrate MFA connection strings.
PAM Username#Your MFA code#Unique PAM Record Name or ID
bwilliams#278461#Windows Production Server
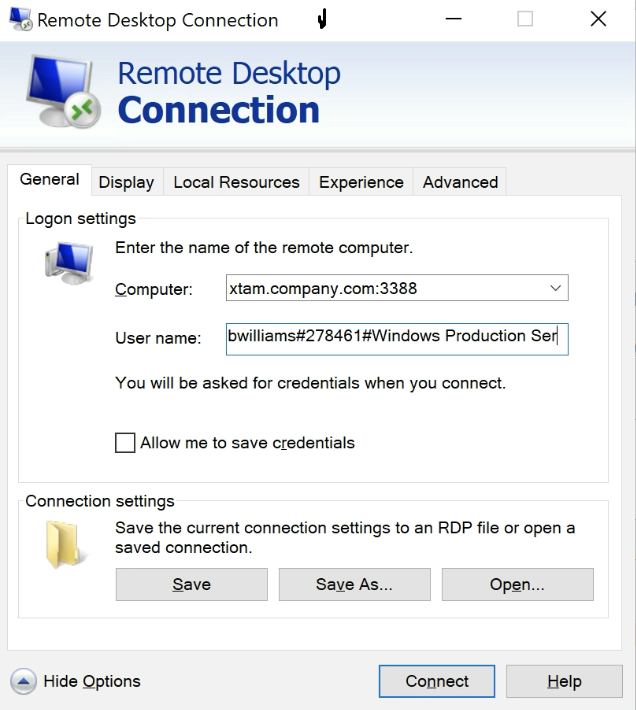
The 278461 represents an example of your TOTP token.
PAM Username#Duo type or passcode#Unique PAM Record Name or ID
bwilliams#auto#Windows Production Server
bwilliams#push#Windows Production Server
bwilliams#phone#Windows Production Server
bwilliams#397623#Windows Production Server
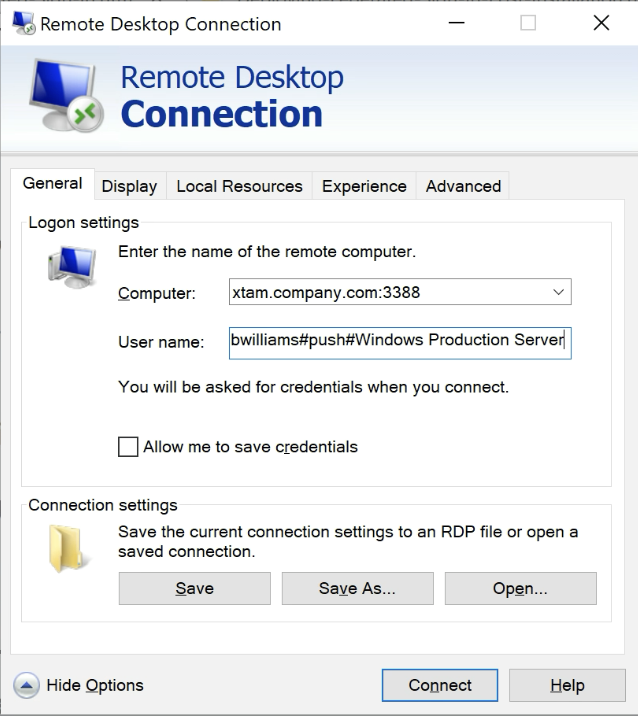
The auto type will use your default Duo method, the push type will send a Duo Push to your registered device, the phone type will generate a phone call to your registered device and the 397623 represents an example your unique Duo Passcode. SMS is not supported because there is no prompt to enter the code after it is generated.
Please note when using either the auto, push and phone options, the connection process of the RDP Proxy will pause until you Approve the Duo challenge on your registered device.
Note that the Type RDPP indicates a RDP Proxy Session whereas the Type RDP indicates a RDP Web Session.
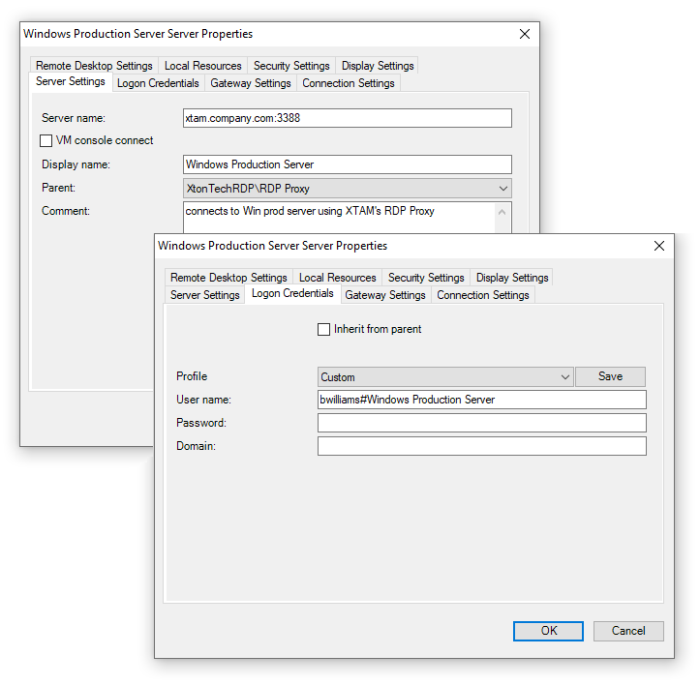
Example: Remote Desktop
Example using Remote Desktop Connection Manager.
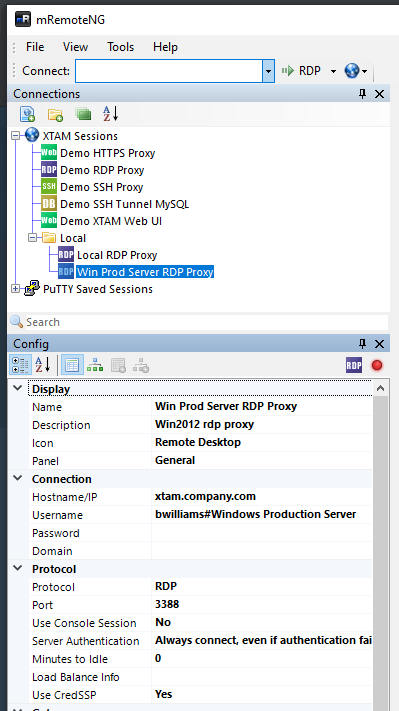
Example: mRemoteNG
Example using mRemoteNG.
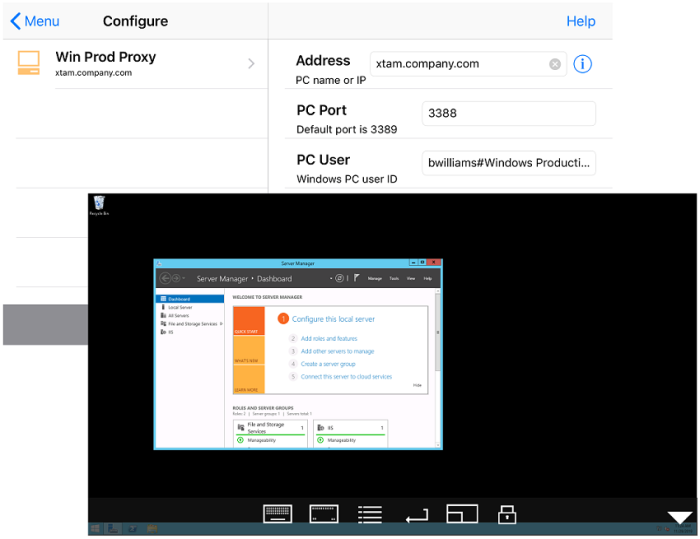
Example: generic RDP Mobile App
Example using a generic RDP Mobile App.
Troubleshooting
RDP Proxy connections troubleshooting:
- In PAM GUI search using the query: computer name. Does the search one single Windows Host record?
- If the search finds no records or several records, try to connect to the record using Record-ID (you can grab it from the Record view screen) that you can use after # sign.
- If only one record is found, can you connect to this record using WEB RDP Session?
Contact the Support team and share a screen shot of the record view so we can check whether it has user or $login for pass-through connection.
- If WEB Session does not connect check the password on record is correct or PAM server does not have a connection route to the destination server.
- If PAM is on a Windows computer, can you connect to the destination server using a native RDP client from PAM computer?
- If you use $login as a User name then try to use a real user name and password to test the connectivity.
- On PAM GUI using login name navigate Management > My Profile > Re-Enable RDP Proxy. Enter password > Save.
- Try to perform the RDP Session connection again. Does it work now?
- Did you enable RDP Proxy in Administration > Settings > Global Parameters screen?
- RDP Proxy is disabled by default. After enabling it, please restart service pammnager / PamManagement and try to connect again.
- Is it possible that port 3388 is closed on PAM host server firewall or on the route to it (AWS Security Group or Azure NG)?
- Please reopen a port and try to connect again.
- Finally, if nothing works or gives a clue how to proceed, please contact the Support team and send all log files from the folder $PAM_HOME/web/logs.