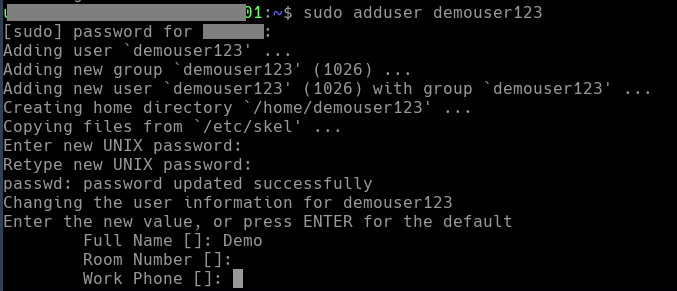
Session Event Masking
In some situations, it may be necessary for a user to type or paste a password during a recorded remote session.
Although such actions are not recommended, unfortunately it might be required.
As a result, session event recording, when enabled, will capture such KeySequence and Clipboard events and display this password in its report, potentially viewable by other privileged PAM users.
In an attempt to prevent user typed passwords from being visible in a Session Events Report, PAM can apply a password detection algorithm to the content of the report.
This feature attempts to detect single word events that most likely are a password and in response, mask them from the report making it unviewable by all users.
Masking Conditions
Before you consider enabling this feature, you should understand how the algorithm processes perceived passwords and the conditions in the function.
When enabled and a Session Event Report is accessed, the Password Detection Entropy is applied to all events captured in the report, using the following conditions, before it is viewable:
-
It will evaluate KeySequence and Clipboardevents for potential masking. KeySequence events represent keystroke recording or someone using a keyboard during a remote session to input text, while a Clipboard event would represent someone pasting a potential password into a session. This will work for any PAM remote session that supports native event recording including RDP web or proxy and SSH web or proxy types.
-
It will only evaluate single word events. This means that if an event contains multiple words, then it is not evaluated and this entire KeySequence or Clipboard event will remain unmasked. Single word events are more likely to be a user typing in a password at a prompt or pasting one into a session using the clipboard, followed by an Enter or Tab command rather than a series of words likely representing commands or parameters.
-
It will only evaluate single word events that are longer than 8 characters. Even a minimally secure password should be at least 9 characters long so the likelihood of a 4- or 6-character string being a password is significantly less. If you use passwords that are less than 9 characters, we strongly recommend you increase the length and complexity of your password policy for many reasons beyond the use of this feature.
If all the above conditions are satisfied, the Password Detection Entropy algorithm will be applied to the recorded Session Event.
Password Detection Entropy Configuration
When the algorithm detects a perceived password in the Session Event Report, it will prevent the password event from appearing in the report and instead, display a series of asterisks indicating that it is a masked event. This prevents all users from viewing the recorded event.
To configure Password Detection Entropy:
-
Login to PAM using a System Administrator account. Only System Admins may enable/disable and configure this feature.
-
Navigate to Administration > Settings > Parameters > Password Detection Entropy.
-
Set a numerical value into this parameter and click its Save button. The next section of this guide describes the concept of this value.
-
Open a Session Events Report to evaluate the results and adjust the entropy value as required. If adjustments are required because a known password is visible or non-password values are masked, change the value, click the Save button again and refresh the report to see the updated results. You do not have to create newly generated Session Events to observe the results of an updated entropy value.

Tip: If a known password is unmasked, your entropy value is too large and should be decreased to adjust for the less complex nature of that password. If a known password is masked and known non-password events are also masked, your entropy value is too small and should be increased to find the middle ground between the two (i.e., password masked, non-password unmasked). There is a mix of art and science (and trial and error) in determining the appropriate value for your password detection.
Entropy Value Description
There is no universally correct entropy value, so expect a bit of trial and error in finding your middle ground.
To understand how the numerical range operates, let us begin with the value.
First, to disable this feature enter a 0 (zero) value into this parameter and click Save (disabled is the default state).
When disabled, no Session Events will be processed, and all recorded events will be visible in the report.
When any value greater than 0 is saved to the parameter, the feature will be enabled, and the supplied value will be used.
Now, how to determine which value to use must be understood in conjunction with the algorithm, beginning with the previously mentioned conditions. When a single word KeySequence or Clipboard event greater than 8 characters is present in a Session Events report, the algorithm assumes it is a password regardless of the parameter’s non-zero value.
It starts evaluating with the assumption that it is a password and not, for example, a PowerShell or Linux command.
Next, it processes the strength of this perceived password using the value entered to this entropy parameter.
This considers the probability that it is a password, and not a command, based on characteristics like randomized characters, dictionary checks and several other methods.
As a result of the processing of the event, the algorithm generates a numerical value for each of these events relative to its complexity.
If the resulting numerical value of the processed event is greater than the Entropy parameter, PAM determines it is a password and is therefore masked from the report.
Conversely, if the numerical result of the processing is less than the Entropy value, PAM determines it is not a password and therefore is not masked.
To further illustrate this, use the example of an Entropy value set to 50. If a single word event is processed and returns a value of 15, PAM determines this is not a password because if it were, it would represent a very ‘weak’ password and therefore likely it is a command that should not be masked.
However, an event that returns a value of 80 would indicate that this value is complex compared to a 50 valued event and therefore highly unlikely, under these conditions, to be anything but a password so it is masked.
The ”trial and error” aspect of determining the ideal Entropy value is required so that it masks passwords and does not make other non-password events.
And if such an exact middle ground value does not exist, then considerations would need to be made to determine if a lower value would be more ideal to ensure passwords are masked with the understanding that some other single word non-password events may also be masked.
Password Detection Entropy Example
The following example intends to provide a demonstration of this feature.
A user starts a remote Windows session (RDP) where session event recording is enabled.
When running a PowerShell command, the user is presented with a password prompt where they type in the required password to execute the command.
Due to the user’s session having event recording enabled, this event is captured and included in the Session Events report displaying the password they typed in the prompt.
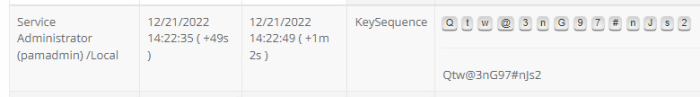
However, with a Password Detection Entropy of 60 applied, this single word event is determined to be a strong password and is masked from the report, while the remaining non-password event, the PS command, remains unmasked.
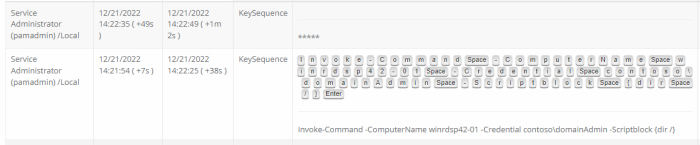
A similar example could be presented with login credentials used for a website on a remote session or during a SSH session where a user who knows the root or sudo password and types it when prompted.
The Password Detection Entropy feature is applied to the Session Events report meaning any PAM remote session protocol or type can support password masking.