Rotating Domain Service Account Passwords in Additional Domains using LDAP Server and LDAP User Records
This article describes an example configuration that can be used to reset a password of domain service accounts in non-primary Active Directory domains.
Non-primary domain refers to a domain that is not used for Active Directory integration with PAM.
- Login to PAM with a System Administrator account.
- Navigate to Administration > Records Types.
- Locate and select the Record Types LDAP Server and LDAP User, then click the Bulk Actions dropdown and choose Enable.
- This will make both Record Types available to be used as Records in PAM.
- Create the following folder structure. Note these folders are used as an illustrative example and it is not required to create them for the password reset operation to be successful.
- LDAP
ADUsers
ADAdmins
DomainControllers
ServiceAccounts
-
In the ADAdmins folder, create a record using the Active Directory User type and, in this record, enter your Domain Admin account credentials.
-
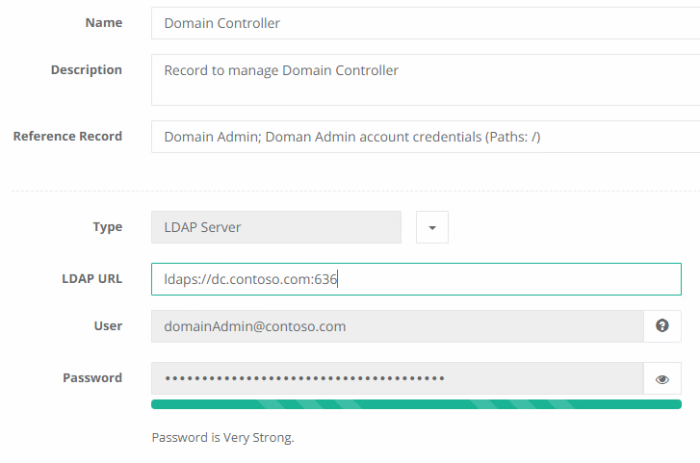
In the DomainControllers folder, create a record using the LDAP Server type that is used to connect to this non-primary domain. Specify the LDAP URL for this domain controller and for credentials use the Reference Record field to reference the Active Directory User record created in the previous step. Note that the LDAP URL must use a secure LDAPS connection like this example: ldaps://dc.somedomain.com:636.
-
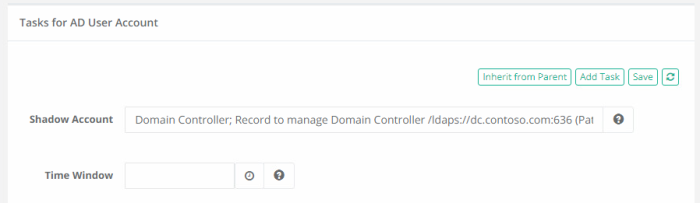
In the ADUsers folder create a record using the LDAP User type. This record will contain the LDAP account which will have the password rotated. Specify the LDAP account using UPN format like this example: username@somedomain.com. Additionally, in this record, navigate to Manage > Tasks, click the Make Unique button and in the Shadow Account field, select the LDAP Server record that was created in a previous step in the DomainControllers folder. Finally, click the Save button.
-
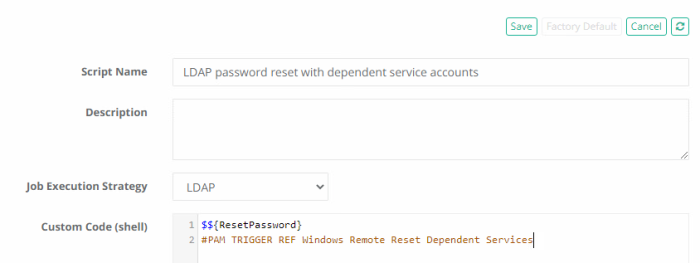
Next, we will create the script that processes the password reset operation. Navigate to Administration > Scripts and click the Create button. On the script create page, enter the following values and Save when complete:
- Script Name: LDAP password reset with dependent service accounts
- Strategy: LDAP
- Custom Code:
$${ResetPassword}
#PAM TRIGGER REF Windows Remote Reset Dependent Services
Now, we will return to the records and continue our configuration.
-
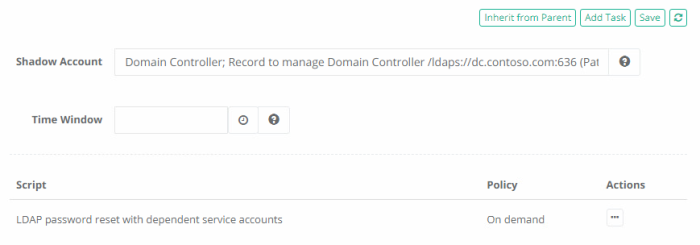
In the ServiceAccounts folder create a record using the LDAP User type. This record will contain the LDAP credentials of the service account that is being managed. After this record is saved, navigate in it to Manage > Tasks and click the Make Unique button. Add the LDAP Server record created in an earlier step as the Shadow Account and click Save. Then, click the Add Task button, select the custom script LDAP password reset with dependent service accounts that was previously created, check the On Demand event option and finally the Save button.
-
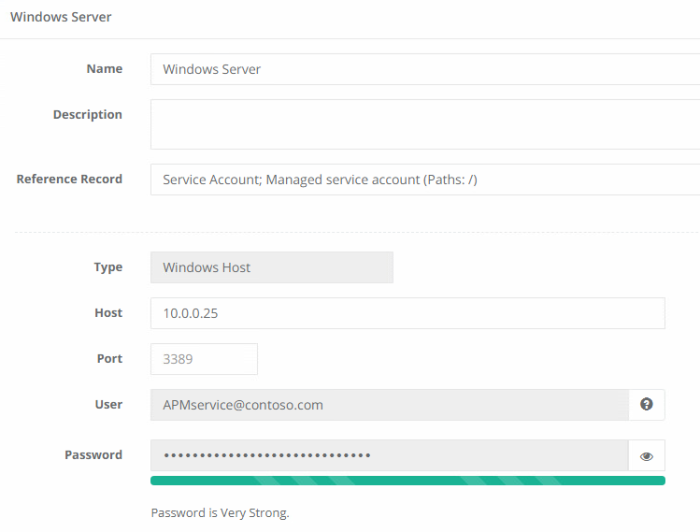
Return to the ServiceAccounts folder and create a record using the Windows Host type. This record(s) will represent the host(s) where the Service Account is present and where the service itself is running from that is being managed. In this Windows Host record, set the Reference Record field to be the LDAP User record that was created in the previous step in this same folder. Enter the appropriate value in the Host field (hostname, FQDN or IP address) and then click Save and Return.
-
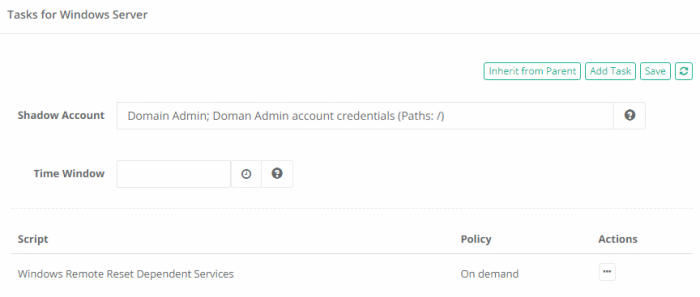
From within this new record, navigate to Manage > Tasks and click Make Unique, then in the Shadow Account field select the AD Admin account from the record created earlier in the ADAdmins folder. Finally, click the Add Task button, select the script Windows Remote Reset Dependent Services, check the On Demand event option and finally the Save button.
-
This completes the configuration and we can now test the process. To execute the operation, open the LDAP User record created in the ServiceAccounts folder and execute the on-demand script LDAP password reset with dependent service accounts. After this password is successfully changed, the Service Accounts update will be triggered on each Windows Host record where this service account was set as the reference record.