Transparent Perimeter deployment
Transparent Perimeter deployment option provides access to closed isolated networks behind firewall based on the reverse tunnel architecture.
The option improves security of the isolated network under management by allowing external parties to access assets inside the network with no requirements to open ports in the network firewall.
Transparent Perimeter deployment is a useful addition to an MSP looking to manage client networks with no interference with the network perimeter.
The option is also useful for organizations accessing on-premises or multi-cloud data-centers using cloud-deployed Master PAM cluster.
The Transparent Perimeter feature complements the existing Remote Node deployment scenario that requires a firewall rule to open the port in the isolated network to provide secure encrypted Master Node connectivity to the Remote Node.
For Windows 10 hosts the optional feature OpenSSH Service should be enabled following these instructions.
Remote Worker Nodes for multiple Master Nodes
Remote Worker Nodes are able to service multiple Master Nodes.
This option allows organizations to architect efficient access network servicing assets hosted at the same cloud datacenter to independent clients.
This function is useful for an MSP providing access to assets of multiple clients hosted at the same datacenter to several internal or external groups managing those assets.
In this case, one single remote node cluster inside the datacentres will serve all groups each with the independent master nodes interested to manage these assets.
The function also provides MSP with the cost-efficient option to gradually migrate managed assets from multiple clients datacenters into a hosted cloud location reusing the access infrastructure of a hosted cloud network.
Use the following configuration on the remote node to configure multiple master node connections.
- xtam.remote[0].enabled = Flag to enable master node configuration for multi-master node deployment
- xtam.remote[0].url = Master node URL in multi-master node deployment
- xtam.remote[0].user = Master node user in multi-master node deployment
- xtam.remote[0].password = Master node password in multi-master node deployment
- xtam.remote[0].token = Master node password token in multi-master node deployment to use instead of user and password
Note that the index in the master node configuration allows specifying multiple connections.
Also, note that the default configuration is given by xtam.remote.* parameters are still necessary and used to designate a primary master node connection to serve as a main monitoring point for the remote node.
Transparent Perimeter
The Transparent Perimeter feature might be used to provide low level traffic connectivity to networks with high security requirements or to quickly investigate test scenarios.
This deployment scenario requires hosts of PAM Master nodes to provide SSH Tunneling capability for the remote node.
In this configuration, PAM Remote Node deployed to the closed isolated network builds and maintains reverse SSH tunnels back to the master nodes using configured port on the master node.
It allows administrators to configure Session Manager Proximity Group in PAM Master node for the localhost port exposing remote session manager inside the isolated network.
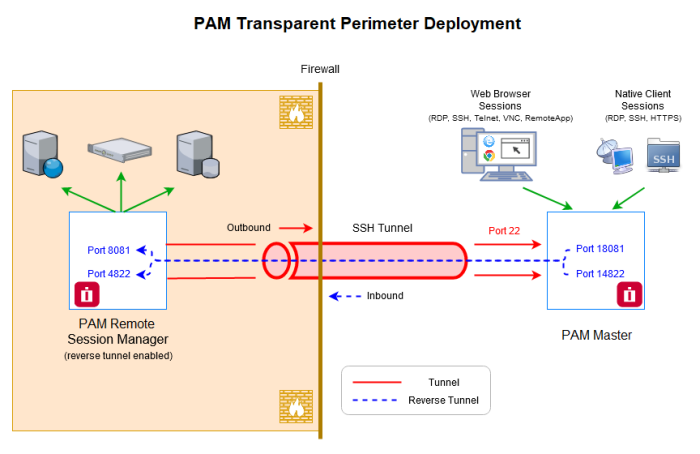
Note that in order for a user to be able establish a connection from Session Manager node (remote node) to the PAM master node, a user should be part of OS local account. Whatever user is listed in xtam.reverse.tunnel[0].remoteUser in catalina.properties should be added in OS level on the master nodes (not PAM).
The configuration for the reverse tunnels is performed using the following properties on the remote node in $PAM_HOME/web/conf/catalina.properties file:
- xtam.reverse.tunnel[0].remoteHost=Master node host for SSH connection
- xtam.reverse.tunnel[0].remotePort=Master node port for SSH connection
- xtam.reverse.tunnel[0].remoteUser=Master node user for SSH connection
- xtam.reverse.tunnel[0].remotePassword=Master node user password or Private Key password for SSH connection
- xtam.reverse.tunnel[0].remoteKey=Path to master node Private Key for SSH connection as an alternative for remoteUser
- xtam.reverse.tunnel[0].forwardHost=Session manager host in the isolated network in the local isolated network space
- xtam.reverse.tunnel[0].forwardPortLocal=Session manager port in the isolated network
- xtam.reverse.tunnel[0].forwardPortRemote=Session manager port on the master node to use in the proximity group
- xtam.reverse.tunnel[0].forwardBindingAddress=Binding address on the master node to expose the port to other interfaces
xtam.reverse.tunnel[0].aliveInterval=Sets the server keep-alive interval property in milliseconds. If 0 is specified, no keep-alive message will be sent. The default interval is 10000.
xtam.reverse.tunnel[0].aliveCountMax=Sets the number of keep-alive messages which may be sent without receiving any messages back from the server. If this threshold is reached while keep-alive messages are being sent, the connection will be disconnected. The default value is 20
Note that index in xtam.reverse.tunnel configuration allows to specify multiple tunnels maintained by the remote node. Reverse tunnel SSH connection could be established using user / password or user / private key (optionally with password).
In addition to reverse tunnel, the node is capable to establish and to maintain forward tunnel to the master node to limit all traffic from the remote node to the master node to SSH tunnel port 22 including HTTPS traffic from remote worker to the master node as well as reverse traffic from the master node to remote session managers.
The option further simplifies remote network requirements for the remote node configuration.
The configuration for the forward tunnels is performed using the following properties on the remote node in $PAM_HOME/web/conf/catalina.properties file:
- xtam.forward.tunnel[0].remoteHost=Master node host for SSH connection
- xtam.forward.tunnel[0].remotePort=Master node port for SSH connection
- xtam.forward.tunnel[0].remoteUser=Master node user for SSH connection
- xtam.forward.tunnel[0].remotePassword=Master node user password or Private Key password for SSH connection
- xtam.forward.tunnel[0].remoteKey=Optional path to master node Private Key for SSH connection as an alternative for remoteUser
- xtam.forward.tunnel[0].forwardHost=Host in the master node network to forward tunnel to
- xtam.forward.tunnel[0].forwardPortLocal=Forwarded port on the remote node to map as a master node port
- xtam.forward.tunnel[0].forwardPortRemote=Master node port to forward traffic to (usually 443)
- xtam.forward.tunnel[0].forwardBindingAddress=Binding address on the remote node to expose the port to other interfaces
xtam.forward.tunnel[0].aliveInterval=Sets the server keep-alive interval property in milliseconds. If 0 is specified, no keep-alive message will be sent. The default interval is 10000
xtam.forward.tunnel[0].aliveCountMax=Sets the number of keep-alive messages which may be sent without receiving any messages back from the server. If this threshold is reached while keep-alive messages are being sent, the connection will be disconnected. The default value is 20.
Note that index in xtam.forward.tunnel configuration allows to specify multiple tunnels maintained by the remote node. Forward tunnel SSH connection could be established using user / password or user / private key (optionally with password).
Also note that for proper HTTPS configuration the remote node DNS resolution of the master node name should be defined for the local host of the remote node.