Integration with Active Directory in HA mode
To implement an alternative URL (Domain Controller) for Active Directory, perform the following:
- Open for edit $PAM_HOME/web/conf/server.xml. Find PAM AD REALM section there end add this property to Realm configuration: alternateURL="${ldap.alt}"
- Open $PAM_HOME/web/conf/catalina.properties. Search for MS AD configuration section and add the following line replacing ALTERNATE-LDAP-URL with your alternate AD URL:
ldap.alt=ALTERNATE-LDAP-URL
Copyldap.alt=ldaps://dc2.somedomain.local:636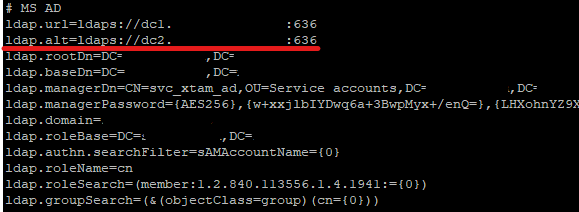
Search for cas.authn.ldap[1] properties group. For deployments using Federated Sign-In component list alternative LDAP URLs space separated in cas.authn.ldap[1].ldapUrl. This property accepts space separated list of domain controllers add necessary controllers there.
Edit parameter like in the example below:
Copycas.authn.ldap[1].ldapUrl=ldaps://dc1.domain.local:636
ldaps://dc2.domain.local:636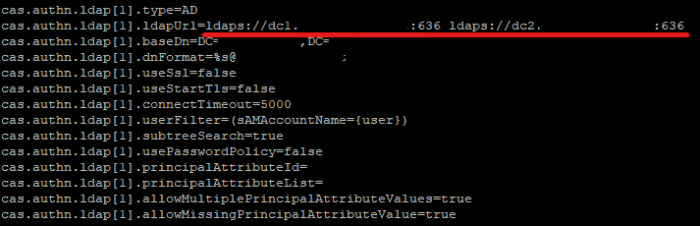
- Ensure that there are no trailing spaces in properties values. Save and close both files.
- Import certificates from all domain controllers to PAM local java keystore on all PAM nodes using PAM CLI Utility PamDirectory SSLImport command. This can be done by issuing followed command from ($PAM_HOME) location:
- Restart PamManagment (pammanager for Linux).
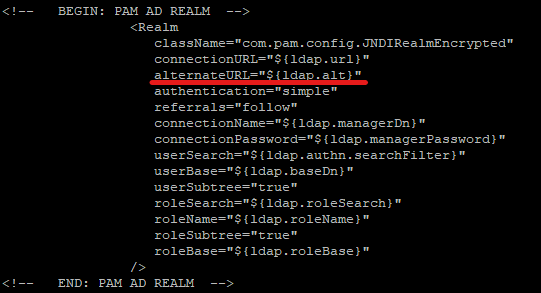
The updated realm specification will look like on the exhibition below:
<Realm
className="com.pam.config.JNDIRealmEncrypted"
debug="99"
connectionURL="${ldap.url}"
alternateURL="${ldap.alt}"
authentication="simple"
referrals="follow"
connectionName="${ldap.managerDn}"
connectionPassword="${ldap.managerPassword}"
userSearch="${ldap.authn.searchFilter}"
userBase="${ldap.baseDn}"
userSubtree="true"
roleSearch="${ldap.roleSearch}"
roleName="${ldap.roleName}"
roleSubtree="true"
roleBase="${ldap.roleBase}"
/>Result will be similar to this screenshot:
bin/PamDirectory.sh sslimport dc1.somedomain.local 636cas.authn.ldap is for CAS authentication (forms based auth and sso).