Azure MSI
Azure Managed Identity, also known as Managed Service Identity (MSI), is a powerful feature that enhances the security of applications hosted on Azure.
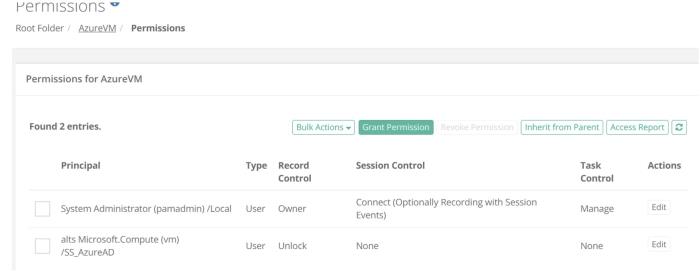
System Assigned Managed Identities can now be discoverable within PAM’s Directory mapping.
This will allow an Azure resource, with a System Assigned Managed Identity, to be assigned permission to PAM records and use an Azure JWT token for authentication.
Requirements
-
Microsoft Entra ID (Azure AD) integration configured with PAM using the following article, https://help.xtontech.com/content/installation/integrations/azure-ad.htm. Copy and save the Client ID of your App Registration which will be used later.
-
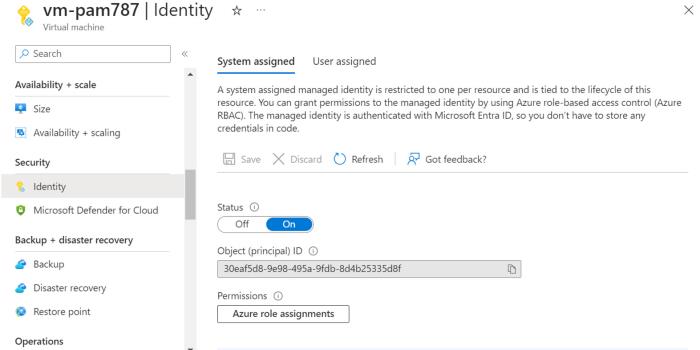
An Azure resource, such as a virtual machine, with a System assigned Managed Identity.
PAM Configuration
-
Following the linked Azure AD guide in the Requirements section of this article, the catalina.properties file will have the Microsoft Entra ID Registered App details to look similar as below.
-
Entra ID Registered app details:
CopyazureAD[0].name={unique name}
azureAD[0].tenantID=00000000-0000-0000-0000-000000000000
azureAD[0].clientID=00000000-0000-0000-0000-000000000000
azureAD[0].secretValue={AES256},{85dMf0bkaTVHjM27pR6l4yHRzSU=},{vuErr/+HSD/RdKFqmtSioQ==},{AgDH35leDji01KJ2jHnhV8FKU0g8xZW+N+RVbMKmGbLrraqkooqhiOy+nsH//7nO} -
Add the following property to enable searching for Managed Identities in PAM:
Copyxtam.landing.azure_auth=true
-
-
If MFA (Multi Factor Authentication) is configured, ensure the MFA for the Managed Identity is set to None and individual MFA configuration is enabled. Please review this article for more information about this step: https://help.xtontech.com/content/administrators-and-power-users/mfa-configuration/defining-mfa-per-user-or-group.htm.
-
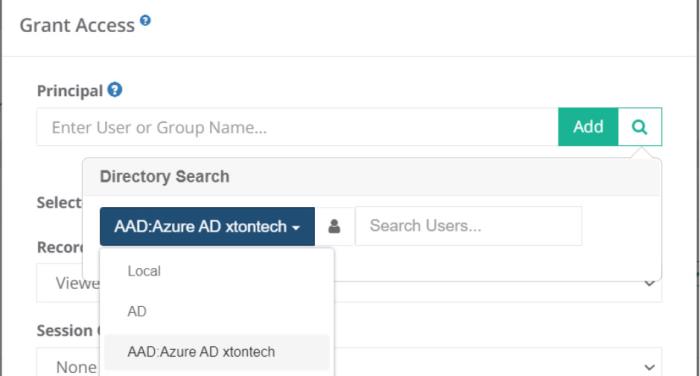
Assign the required permission to the System assigned Managed Identity for the PAM records. From the Permission assignment module, use the directory search option and select the Microsoft Entra ID (Azure AD) choice that begins with ‘AAD:’. Use the Search Users... option to find and assign the Managed Identity.
Steps for Implementation
-
Generate a JWT token from the Azure VM directly using your System Assigned Managed Identity:
-
Authenticate with the Azure JWT token and retrieve a session cookie for PAM
-
Call the required PAM API. For this example, it is requesting an unlock of a PAM record:
Copycurl -k -X GET https://<PAM HOST>:6443/xtam/rest/record/unlock/<RECORD ID> \
-b pam.cookies $@
curl 'http://169.254.169.254/metadata/identity/oauth2/token?api-version=2018-02-01&resource=xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx' -H Metadata:true -s
The resource is the value of the Client ID from the App Registration.
curl -k -X POST https://<PAM HOST>:6443/xtam/landing\
-H "Content-Type: application/x-www-form-urlencoded"\
-c pam.cookies \
-d "azure=$JWT" $@Output
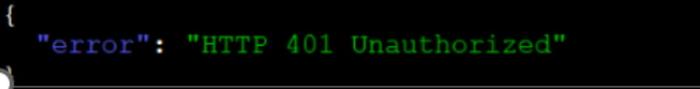
Without proper permissions granted to a PAM record you should expect an error response like shown below:
{
"error": "HTTP 401 Unauthorized"
}
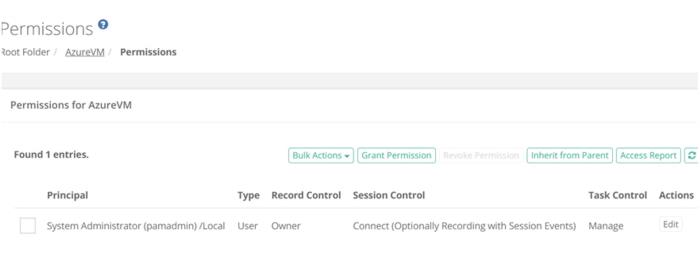
With proper permissions granted to a PAM record you should expect a successful response like shown below: