Imprivata Manage EAM Admin AD
PAM supports secure management and rotation of the EAM AD accounts.
The following guide describes how to configure your PAM and EAM integration to rotate the EAM Admin AD account.
Requirements
Before you begin your integration, be sure you meet the following pre-requisites:
-
A working PAM deployment with the Federated Sign-In experience.
-
The version of PAM must be Release 2.3.202504* (April 2025) and beyond.
-
Access to your existing PAM host server. You will need to update files and restart services.
-
Access to your EAM admin console to retrieve the AD account.
-
If Users are synced from Active Directory to EAM, then you must also integrate PAM with the same Active Directory.
-
Ensure that ldaps is configured (otherwise it does not work).
If the AD account used for syncing AD account in EAM does not have sufficient rights, you will need to make this account a member of a security group that has sufficient rights (or add a Shadow Account with sufficient rights to the EAM AD record Type you created under Step 2 point 2) to allow the execution of this task.
Step 1: Retrieve the AD account from Imprivata EAM
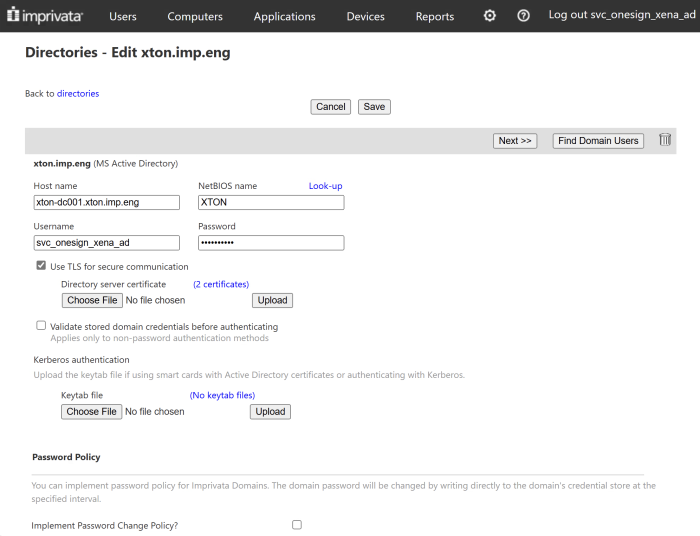
The AD account used to sync AD users in EAM can be retrieved by navigating to User > Directories > Domain on the EAM admin page.
Step 2: Configuring PAM record to rotate AD account on EAM
-
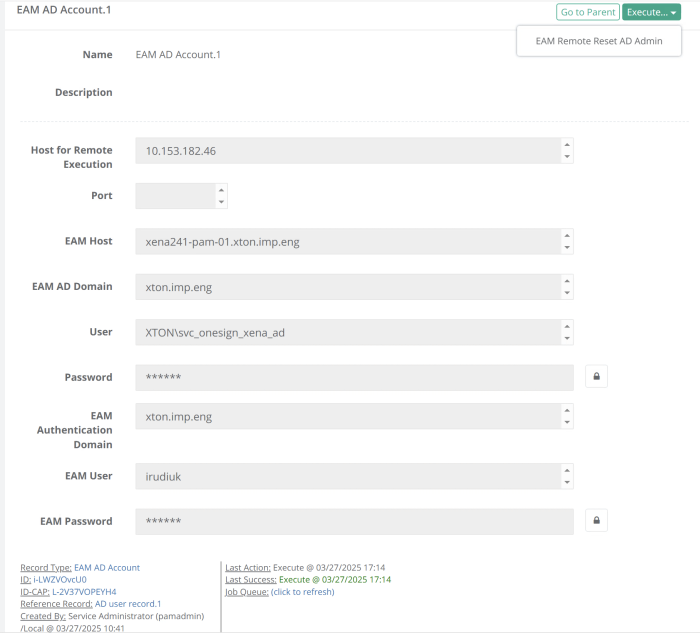
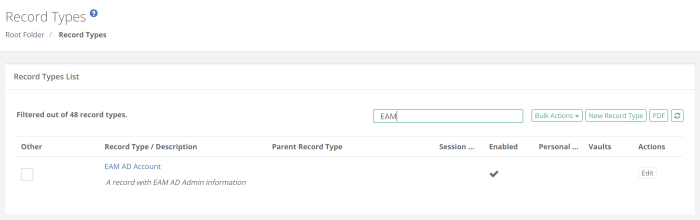
Add a new record with Record Type EAM AD Account. In case this record type is not visible, navigate to Administrator > Record Types, edit EAM AD Account and uncheck the hidden checkbox.
-
The EAM AD record type requires the following input fields:
-
The script to update the EAM AD account passwords has to run on a windows host. The host information is provided in the following fields:
-
Host for Remote Execution
-
Port
-
-
AD user details to login to the Windows host. This is also the AD account configured on EAM should be the same user as the EAM AD account used to sync AD as mentioned in Step 1:
-
EAM AD Domain
-
User
-
Password
-
-
Details for PAM to authenticate to the EAM server:
-
EAM Host - EAM appliance FQDN
-
EAM Authentication Domain
-
EAM User - EAM admin console administrator user
-
EAM Password
-
-
-
Task to execute:
-
The EAM AD Account can be reset by running the EAM Remote Reset AD Admin task.
-
AD Password Reset task
Steps to configure the EAM AD Account task as a dependent task of an AD Password Reset task.
In most cases, Imprivata PAM will have a record to manage the AD account under a Active Directory User record. In order to trigger the EAM AD account reset on successful rotation of an AD account in PAM, follow the steps below.
-
Configure a record to rotate the AD account in PAM, using the same AD account as mentioned in Step 1 by creating a new Active Directory User record.
-
Create a custom Password Reset LDAP task and customize the task by updating the script to include a reference of the EAM AD Account task. Alternatively, you could also create a custom task and add it to the record.
-
Edit the EAM AD Account record by setting the above Active Directory User record as a reference record. The User and Password fields will be set from the referenced record.
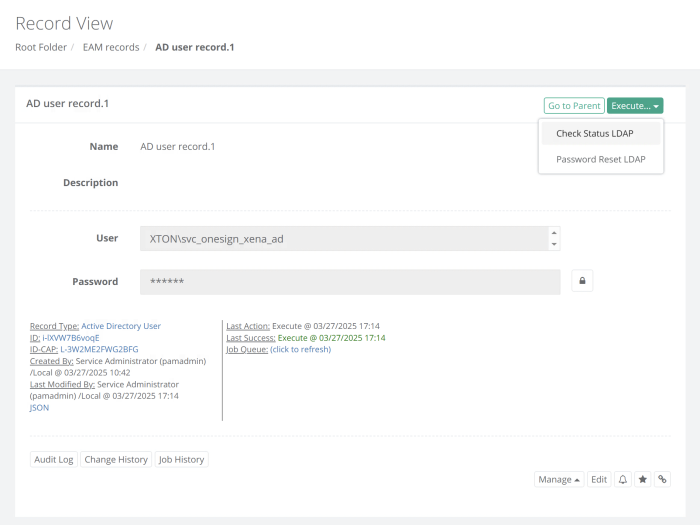
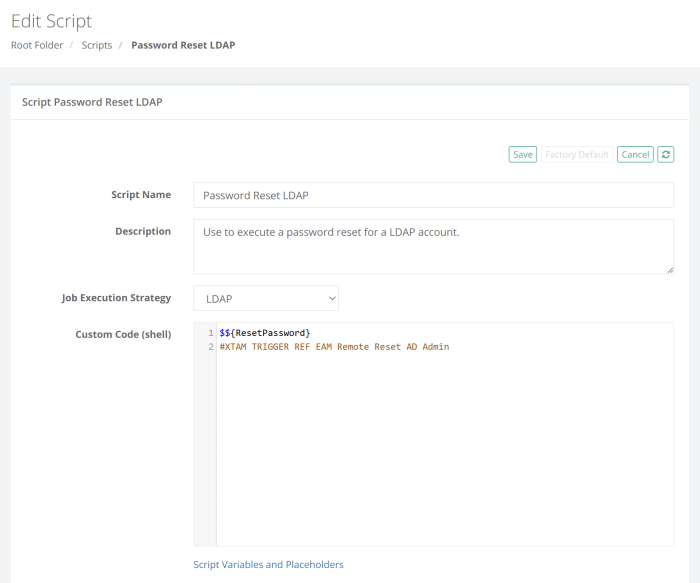
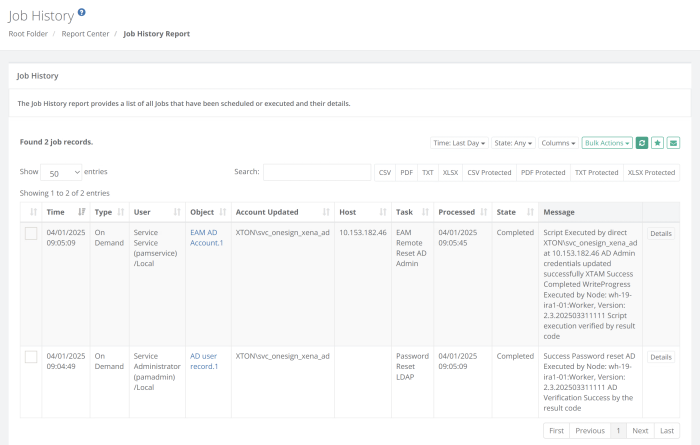
When the Password Reset LDAP task associated to the Active Directory User record runs, PAM reads the script and upon successful completion of this task, will trigger the EAM Remote Reset AD Admin task that is referenced in this record to be scheduled and executed. In the Report Center > Job History report, the parent task as well as the referenced tasks will be visible.