Secure Web (HTTP) sessions using your native browser [Deprecated]
This feature has been deprecated and is no longer supported. For web site sessions, please use either the Browser Extension for login filling or a Remote App for secured sessions.
Privileged Access Management can secure your Privileged Web Sessions.
Access Manager provides quick, easy and reliable methods to create secure, password-less sessions to remote endpoints using the most common protocols like RDP, SSH, VNC, Telnet and others.
We are pleased to now also support the same secure and password-less session capability for web sites or web based applications using HTTPS like Github, Office 365, Twitter or your own custom built solutions.
No matter if you are a marketing company looking to provide more security around your client’s social media accounts like Twitter, Facebook or Instagram, an accounting department needing to access confidential finance or billing portals or if you are attempting to provide more security around your production logins to sites or applications like Github, Office 365 Global Administrators, Service Now or Salesforce, then Access Manager’s HTTP Proxy Broker is what you need.
As IT or Security Department team members, you can now grant access (directly or with approval workflows) to web sites and applications without disclosing the secured login credentials to your privileged users.
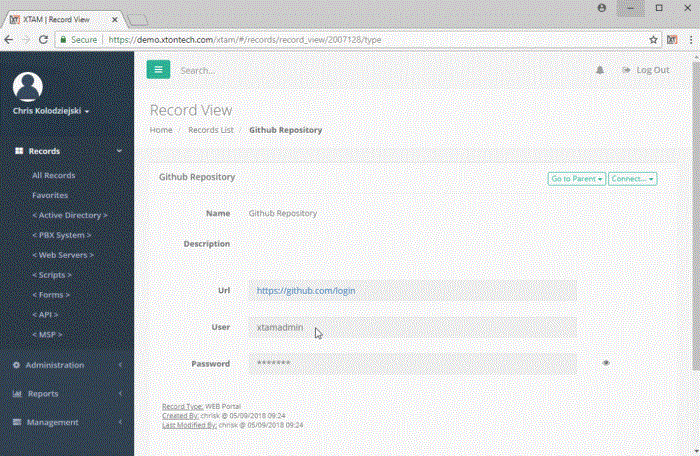
User’s will Connect to the website in the Access Manager record and when the site’s login page is loaded, they will enter a username and password that is centrally configured and secured in Access Manager’s password vault.
This Access Manager placeholder credential will allow the site’s login page to process the request and then Access Manager will exchange the placeholder credentials during authentication with the actual login credentials from the record, completely invisible to the end user.
In the end, they will be securely logged into the site using the credentials from the Access Manager record without these same values being disclosed to them.
HTTP Proxy Concept
Understanding the HTTP Proxy Concept in Access Manager.
Before we begin with the setup, configuration and use of the Access Manager HTTP Proxy feature, let’s describe how it is designed to work.
Take a look at the following architecture diagram and then scroll down for an explanation of each component.
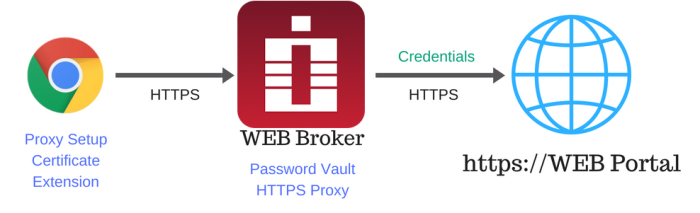
Starting on the left side, the Google Chrome icon is used to depict a user’s client browser. In their browser, a proxy is configured, an Access Manager certificate is deployed and optionally the Access Manager Browser Extension is installed.
- Proxy Setup: The proxy is configured so that when a user attempts to reach a specific domain, the request is redirected back through Access Manager. This enables Access Manager to provide the secure, password-less access to the web portal.
- PAM Certificate: This enables the communication between the user’s client browser, Access Manager and ultimately the web portal is secured.
- PAM Browser Extension: Optionally, the user or Administrator may deploy the extension to automatically configure the proxy configuration in the user’s browser.
The middle section of the diagram is Access Manager which contains the Password Vault and HTTPS Proxy functionality.
- Password Vault: The password vault stores the URL, User and Password values that are used by Access Manager to authenticate against the web portal.
- HTTPS Proxy: This module is designed to create the proxy connection to the domain, replace the user’s entered Placeholder credentials and then switch them to the actual web portal credentials during authentication.
The final section is the actual web portal. Access Manager will supply the actual login credentials from the Web Portal record in the password vault to the web portal, which will then authenticate and login the user.
To summarize the process, the user Connects to the web portal using the Access Manager record, they enter the Access Manager placeholder credentials into the login form and click Login.
Access Manager replaces the placeholder credentials with the actual web portal credentials and then proceeds to login the user.
Now that the concept has been presented, please continue reading our guide so that you can setup, configure and use Access Manager’s HTTP Proxy feature in your deployment.