MFA Configuration Options
PAM supports RADIUS for authentication which most MFA providers utilize in their own solutions; therefore many MFA products can be successfully integrated with PAM.
PAM integrates with your existing MFA provider, it does not provide its own service. Therefore, you will need to follow the configuration guides below before you can configure your MFA usage in PAM. This includes deploying the required Federated Sign-In Module as well as having an Administrative account with your MFA provider.
Configuration Options
The MFA Configuration Options allows a PAM System Administrator to determine which users or groups will have to authenticate using their MFA provider in order to login.
To start using MFA, please first read enabling granular control over MFA configuration for different users or groups of users article to configure PAM to support this feature.
NOTE: The general use of MFA authentication in PAM requires certain pre-requisites to be installed and configured on the host server. Please review the MFA guides located on our website for information regarding these requirements.
To assign an MFA provider to a user or group
-
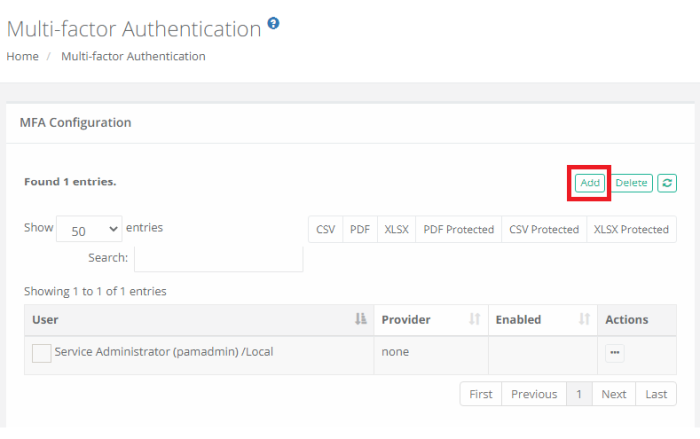
Navigate to Administration > MFA and click the Add button.
-
On the New Multi-factor Authentication page, configure your MFA as required.
|
Add |
Select a user or group that will be added to PAM MFA configuration. |
|
Edit |
Modify PAM MFA configuration of the selected user or group. |
|
Delete |
Remove the selected user or group from PAM MFA configuration. |
|
Default |
When selected, this specific configuration becomes the default MFA provider for all users or groups. In turn, the specific users or groups added separately then become exceptions to this default provider. |
|
Principals |
User or Group to assign to this provider.
This Principals option is removed when the Default option is enabled because default applies to all principals. |
|
Provider |
Select the MFA provider from those available in the dropdown list.
The list of providers in this menu is populated based on the MFA integration(s) that have been established with PAM.
Of note, the none option will result in no MFA authentication being required for the selected principals and the mfa-generic option is used exclusively for token enforcement during SSH Proxy sessions only. |
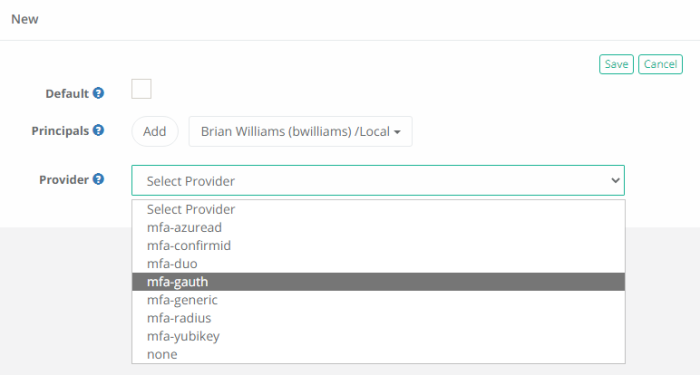
- Click the Save button to complete your MFA configuration.
The mfa-generic provider option enforces the requirement of a mfa token when a user establishes a desktop client SSH Proxy , RDP Proxy, and Oracle Proxy sessions only; it does not generate mfa tokens for any other login or connection purposes. These mfa generic tokens are generated in Management > My Profile > Preferences > MFA Code and have a 3 minute expiration time.
By default, all principals with the System Administrator role are added with no (none) MFA provider configured. This is done to prevent accidental lock out if the MFA integration or configuration is mis-configured. You may change this default behavior if needed.
To edit an MFA provider assignment for a user or group
-
Navigate to Administration > MFA, locate the entry you want to update, open its Actions menu and select the Edit option.
-
On the Edit Multi-factor Authentication page, update the configuration as needed.
-
Click the Save button to complete your updated MFA configuration.
To delete an MFA provider assignment for a user or group
-
Navigate to Administration > MFA, locate the entry you want to delete, open its Actions menu and select the Delete option. For a bulk delete option, check the box next to each entry you want to delete and then click the Delete button located above the Search box.
-
Click the OK button on the confirmation dialog to complete the removal of the selected MFA configuration.
MFA Grace Period
PAM can be configured to allow for a grace period when a user does not receive a native MFA challenge after their initial successful authentication. For security reasons, it is not recommended to enable this MFA Grace Period, however there are some Use Cases and Administrators that may wish to support the user convenience benefits over the security benefits of MFA.
When MFA Grace Period is enabled, the following scenarios will only require a first successful MFA token, after which, the user will not be prompted to provide it again during the time of their defined Grace Period:
-
MFA required Workflow actions like Unlock or Connect
-
Proxy Session authentication like SSH and RDP.
When MFA Grace Period is enabled, the following scenarios will still require a successful MFA token during every attempt:
-
Logins to PAM Web Portal
-
SSO (SAML) logins to PAM will enforce their defined MFA policy as configured in the SSO provider.
To enable MFA Grace Period the following configuration parameters are available and must be configured identically on each Master node in your PAM deployment. In the catalina.properties file, add the following new lines and configure each <parameter> to meet your requirements. After each file is updated, a PAM service restart of each node is required.
#MFA Grace Period
xtam.cas.mfa.bypass.enabled=<true or false>
xtam.cas.mfa.bypass.seconds=<Grace Period Time in Seconds>
xtam.cas.mfa.bypass.ipRange=<Bypass Only for Connections from the Comma Separated Specified IP Ranges>
xtam.cas.mfa.bypass.sharedIp=<disabled or enabled> xtam.cas.mfa.bypass.enabled=true or false
Use true to enable MFA Grace Period and false to disable. This parameter is required.
xtam.cas.mfa.bypass.seconds=<Grace Period Time in Seconds>
Define the amount of time, in seconds, that limits the Grace Period. The grace period begins after the user successfully provides their initial MFA token in the supported scenarios described above. For example, a defined value of 28800 would mean after the user’s first successful MFA validation, they would not be prompted again for 8 hours. This parameter is required.
xtam.cas.mfa.bypass.ipRange=<Bypass Only for Connections from the Comma Separated Specified IP Ranges>
Define a comma separated list of IP ranges that will enforce the Grace Period. Users from within these IP ranges will fall into the defined Grace Period parameters, while others outside of these ranges will continue to be prompted for MFA. This parameter is optional and if not needed, may be removed, or commented out.
xtam.cas.mfa.bypass.sharedIp=disabled or enabled
MFA Grace Period uses a combination of the username and their IP address (at the time of their initial authentication) to determine if this user has previously provided a successful MFA authentication. In the scenario where all users are reported from the same IP address to PAM, this option will allow an Administrator to enable the shared IP configuration. It is not recommended to enable this option unless absolutely necessary. This parameter is required.
When enabled, multiple users presenting from the same IP address will be included in the Grace Period.
When disabled, multiple users presenting from the same IP address will be prompted for MFA regardless of the enabled Grace Period configuration.
MFA Integration
PAM supports RADIUS for authentication which most MFA providers utilize in their own solutions; therefore many MFA products can be successfully integrated with Imprivata Privileged Access Management.
For specific MFA providers, please review the links below:
Duo Security MFA – How to Configure (Admin)
Duo Security MFA – How to Login (Users)
Google Authenticator (or other TOTP providers) – How to Configure (Admin)
Google Authenticator (or other TOTP providers) – How to Login (Users)
RADIUS – How to Configure (Admin)
YubiKey MFA – How to Login to System as a User
If you have a specific MFA or 2FA provider that you would like to inquire about, please contact our Support team: https://support.imprivata.com/.